Search
Items tagged with: technology
#meme #apocalypse #doomsday #collapse #civilization #future #gameover #exitstrategy #problem #endtime #system #matrix #explanation #politics #resources #fight #society #technology #money #finance #rich #wealth #luxury #economy #future #exploitation #billionaire #power #mars #space #solarsystem
(https://opus.ing/posts/how-to-remove-ai-overviews-gmail)

How to Remove “AI Overviews” From Gmail
It’s so easy, there’s no reason not to do it.Jason Morehead (Opus)
8 tiny open source utilities that can instantly make your Linux desktop feel faster
I’d not heard of these apps before, so would be interested to hear if anyone has had good experiences with them?
- Zram-generator
- Preload
- Profile-sync-daemon
- Ananicy-cpp
- Nohang
- Wl-clipboard
- FSearch (had heard of this one)
- Vicinae
See xda-developers.com/tiny-utilit…
#Blog, #linux, #opensource, #technology
_cool, but also concerning... _
https://www.sciencealert.com/computers-made-from-human-brain-tissue-are-coming-are-we-prepared
#technology #brain #computers #computing #bio-hybrid #stemcells #ai #neuroscience #organoid #transhumanism

Computers Made From Human Brain Tissue Are Coming. Are We Prepared? : ScienceAlert
As prominent artificial intelligence (AI) researchers eye limits to the current phase of the technology, a different approach is gaining attention: using living human brain cells as computational hardware.The Conversation (ScienceAlert)
5 open-source projects that secretly power your favourite apps
“You’ve heard that the world’s infrastructure runs on Linux, and how important Free and Open Source (FOSS) software is to just about all the technology we enjoy every day, but there are some (to bring out the old cliché) unsung heroes of FOSS without which your stuff just wouldn’t work—and you should at least know their names.”
It is true, too, that most open source projects are built using other open source projects, but these are a few of those that sit in the background powering many popular projects.
I love the article’s comment about Electron. I suppose it is the same as for Flatpaks, AppImages and Snaps. They make things possible across distros.
See howtogeek.com/open-source-proj…
#Blog, #opensource, #technology
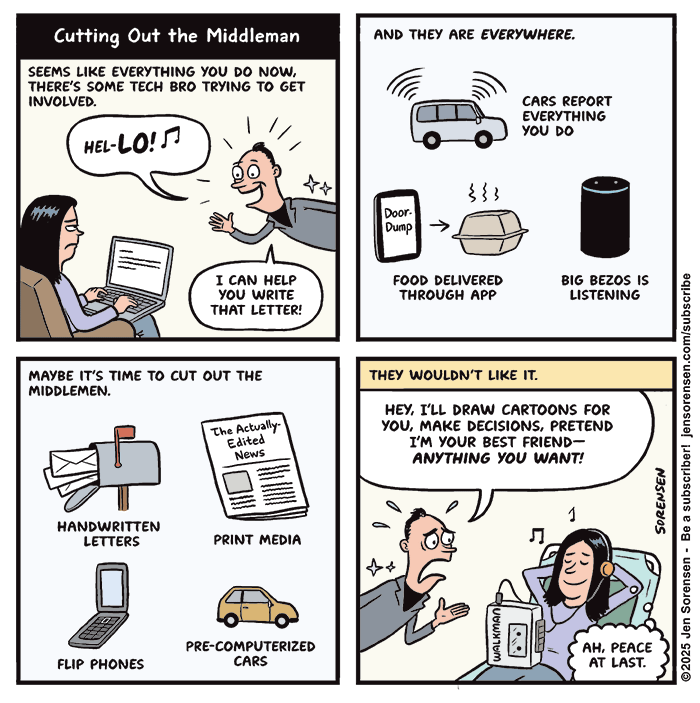
Recent comic: Cutting out the Middleman
I suspect that some readers might interpret this cartoon as a call for Luddism, but mostly it's a reflection of thoughts I've been having lately about out-of-control data harvesting and a growing surveillance state.
#tech #technology #privacy #data #comic #cartoon #surveillance #consumers #corporations
FreeTube ─ Watch YouTube without ads, without login, and with private playlists.
#google #YouTube #privacy #ad #safety #security #InfoSec #data #advertisement #tech #technology #BigTech #app #apps #tip #tips
FreeTube - The Private YouTube Client
FreeTube is a feature-rich and user-friendly YouTube client with a focus on privacy.freetubeapp.io
As someone who is totally blind, the Fediverse is the only place where I have ever been able to follow people such as photographers, artists, or even those who post pictures of their cats or the food they ate. The reason is that most of them use alt text. They take the time to describe the images that my screen reader can't recognise. Some write the descriptions themselves, and others use tools such as altbot. Some worry that their descriptions aren't good enough, especially when they are new at this. Let me assure you, not only are they good enough, they are extremely appreciated! If the rest of the world thought as you did, it would be a much better place. Don't hesitate to ask if you're unsure of something, but never think that we don't notice your effort.
#appreciation #accessibility #altbot #alttext #blind #blindness #fediverse #gratitude #images #inclusivity #peoplewhocare #pictures #technology
"Meta and X are going rogue:" European Digital Rights group (EDRi) urges EU to invest in infrastructure "like Mastodon, Peertube and other key pieces of the Fediverse" to secure Europe's independence
https://edri.org/our-work/meta-and-x-are-going-rogue-here-is-what-europe-should-do-now
#news #tech #technology #socialmedia #twitter #fediverse #politics #europe

Meta and X are going rogue. Here is what Europe should do now. - European Digital Rights (EDRi)
To solve the core problem, we have to curb the immense grip Big Tech has on our institutions and invest in independent digital alternatives.European Digital Rights (EDRi)
Defeating Coordinated Inauthentic Behavior at Scale
Over the weekend, the YouTube channel SmarterEveryDay posted this video (part 1 of a 3-part series) discussing coordinated inauthentic behavior (via crappy content generation) to manipulate YouTube’s…Soatok Dreamseeker (Medium)
It's been interesting reading this #reddit thread. People are understandably upset about the prospect of #youtube showing ads during the pause screen. Lots of people threatening to leave YouTube, but at the end of the day, most won't.
There are alternatives. I've been running #tilvids for over 4 years now. We have great content creators like @thelinuxEXP sharing content. All people have to do is actually start voting with their eyeballs...
https://www.reddit.com/r/technology/comments/1fkbjtk/youtube_confirms_your_pause_screen_is_now_fair/
#tech #Technology #google
"We want to bring organisations and content creators into the Fediverse, step by step."
Our Foundation co-founder has just published an interesting piece on how we're working to help organisations and content creators find their way to the Fediverse!
For more information on what we plan to do as a charity and how Patchwork, a new service we'll be launching soon, can help 👇
https://www.blog-pat.ch/enter-the-fediverse/
#Fediverse #SocialMedia #FediDev #FediAdmin #MastoDev #MastoAdmin #Technology

Organisations and content creators enter the Fediverse
In a Fedicentric world, everything revolves around Mastodon. Mastodon has around 80% of the monthly active users on the Fediverse. Mastodon sets the standard, and is where the action is.Michael Foster (Patchwork Blog)
TROM II: Technology Won't Save Us - https://videos.trom.tf/w/weWXUVT1zXW5v8QRZUG5Lr
#technology #renewables #renewable-energy #electric-cars #capitalism #trade

TROM II: Technology Won't Save Us
Watch the entire documentary here - https://www.tromsite.com/documentaries/trom2/videos.trom.tf
Serbian inventor, electrical engineer, mechanical engineer, and futurist Nikola Tesla was born #OTD in 1856.
Some of Tesla´s inventions and innovations: alternating Current (AC) system; induction motor; Tesla coil; wireless transmission of electricity; radio technology; remote control; neon and fluorescent lighting; X-Ray technology; Tesla turbine; oscillators and frequency generators.
https://en.wikipedia.org/wiki/Nikola_Tesla
Books by Nikola Tesla at PG:
https://www.gutenberg.org/ebooks/author/5067
Books by Tesla, Nikola (sorted by popularity)
Project Gutenberg offers 73,924 free eBooks for Kindle, iPad, Nook, Android, and iPhone.Project Gutenberg
Millions Of #google #whatsapp #Facebook #2FA #Security Codes #Leak Online
Security experts advise against using SMS messages for two-factor authentication codes due to their vulnerability to interception or compromise. Recently, a security researcher discovered an unsecured database on the internet containing millions of such codes, which could be easily accessed by anyone.
#news #tech #technews #technology #privacy

Millions Of Google, WhatsApp, Facebook 2FA Security Codes Leak Online
A security researcher has discovered an unsecured database on the internet containing millions of two-factor authentication security codes. Here's what you need to know.Davey Winder (Forbes)
If what you’re building cannot be built without violating people’s consent, it should not be built.
People can be as upset about this as they want, but so long as they continue to watch #YouTube they continue tacitly supporting their user-hostile actions. If you really want to make a difference, stop watching, and tell content creators why. When you can convince them to move to platforms that don't shove ads down your throat every 3 minutes, THAT is when you'll see #Google change their tune.
#tech #technology #enshitification #PeerTube #tilvids

YouTube’s ad blocker problems are just an Adblock Plus bug
Latest consensus is that YouTube performance issues seem to be Adblock Plus' fault.Ars Technica
So did I mention that no company or government pays me for the work I do?
But you can support my work if you want to live in a world where we have the Small Web as an alternative to the Big Web of Google, Facebook, and other people farmers.
https://small-tech.org/fund-us
#SmallWeb #SmallTech #funding #foss #freeSoftware #openSource #web #dev #tech #technology

Fund Small Technology Foundation
We’re a tiny team of two funded by individuals like you. Your patronage goes towards keeping a roof over our heads as we build a better future for the Internet.Fund Small Technology Foundation
You guys did soldering?! And CAD?!!
A decade later, I had such a class called "technology" in the main curriculum, where we made… a folding wooden bench 🫠️
That said, that bench is very sturdy and practical, and I'm still using it daily two decades later. So there you go, bug-free #technology right there, with an Enterprise-Grade™ lifecycle 🎖️ (I suppose @federicomena would confirm that #woodworking outlasts #electronics and code by a long shot).
Urgent calls.
95d05bb04065013c1b95005056a9545d (900×610) • https://assets.amuniversal.com/95d05bb04065013c1b95005056a9545d
#drabble #phone #technology #humor
Diaspora* Publisher
Share your favourite pages with your Diaspora* friends and receive notifications directly on your browser.goo.gl
Touchscreen card devices may prevent blind customers paying
'Blind customers are being left "frustrated" and "embarrassed" by inaccessible payment devices. Some shops have buttonless touchscreen card readers, meaning you need sight to tap in your PIN'
Very short-sighted tech developers. They should have thought about this, and about the security issues. As should the businesses involved.
https://www.bbc.co.uk/news/disability-67239870

Touchscreen card devices may prevent blind customers paying
Businesses could be breaking the law by failing to make payment machines accessible.By Drew Hyndman (BBC News)
This outcome was pretty important. Companies can't charge you because they hold the copyright to the details of a law.
**Appeals Court Upholds Public.Resource.Org’s Right to Post Public Laws and Regulations Online | Electronic Frontier Foundation** • https://www.eff.org/press/releases/appeals-court-upholds-publicresourceorgs-right-post-public-laws-and-regulations
#technology #law #copyright #copywrong
Appeals Court Upholds Public.Resource.Org’s Right to Post Public Laws and Regulations Online
SAN FRANCISCO—Technical standards like fire and electrical codes developed by private organizations but incorporated into public law can be freely disseminated without any liability for copyright infringement, a federal appeals court ruled Tuesday.Electronic Frontier Foundation
You wouldn’t have McDonald’s teaching your kids about nutrition or Philip Morris teaching them about maintaining a healthy lifestyle. Why are you happy having a surveillance capitalist like Google or Facebook teaching them about technology?
https://www.bbc.co.uk/ideas/videos/surveillance-capitalism-has-led-us-into-a-dystopia/p06p0tdy
#surveillanceCapitalism #technology #web #education #SiliconValley #BigTech

'Surveillance capitalism has led us into a dystopia' - BBC Ideas
Watch the "'Surveillance capitalism has led us into a dystopia'" video at BBC Ideas. Explore other related content via our curated "Futurefest: Occupy the future" playlist.www.bbc.co.uk
If the thing you’re making wouldn’t exist if people had to opt in instead of having to opt out, maybe the thing you’re making shouldn’t exist.

A Ton Of Folks Don’t Know What ‘Right To Repair’ Is, But Strongly Support It Once They Do
In just the last five years, the “right to repair” movement has shifted from nerdy niche to the mainstream, thanks in part to significant support from the Biden FTC and efforts in states like …Techdirt
#tech #technology #news #technews #internet #Brave #Bravebrowser #ChatGPT
https://stackdiary.com/brave-selling-copyrighted-data-for-ai-training/

The shady world of Brave selling copyrighted data for AI training
I'm fairly certain that I was not the only person in the world who thought to himself, "Did they just yoink the entire Internet and bundle it togetherAlex Ivanovs (Stack Diary)
https://www.windowscentral.com/software-apps/googles-going-to-scrape-the-entire-public-internet-to-train-its-ai-tools-and-theres-nothing-we-can-do-about-it
#technology #tech #technews #bot #reddit #tech_news
Google's going to scrape the entire public Internet to train its AI tools and there's nothing we can do about it
The gatekeepers of online content doing what everyone expected.Richard Devine (Windows Central)
https://www.theregister.com/2023/05/12/github_microsoft_openai_copilot/
Discussions: https://discu.eu/q/https://www.theregister.com/2023/05/12/github_microsoft_openai_copilot/
#news #programming #technology

GitHub, Microsoft, OpenAI fail to wriggle out of Copilot copyright lawsuit
Judge won't toss out two key charges, software source slurping case still onThomas Claburn (The Register)
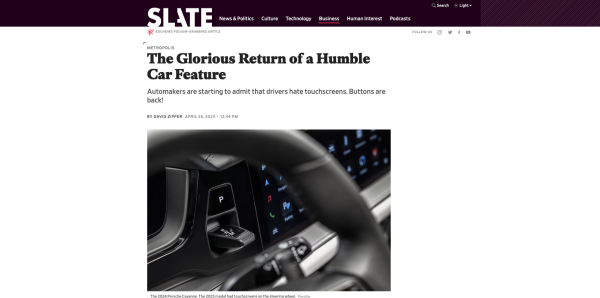
Drivers hate them, and they're also dangerously distracting. Buttons and knobs are poised for a comeback.
My new article in Slate:
https://slate.com/business/2023/04/cars-buttons-touchscreens-vw-porsche-nissan-hyundai.html
#cars #safety #technology
The Glorious Return of an Old-School Car Feature
Automakers are starting to admit that a new car technology didn’t work out.David Zipper (Slate)
Remember when Google's corporate motto was "don't be evil?"
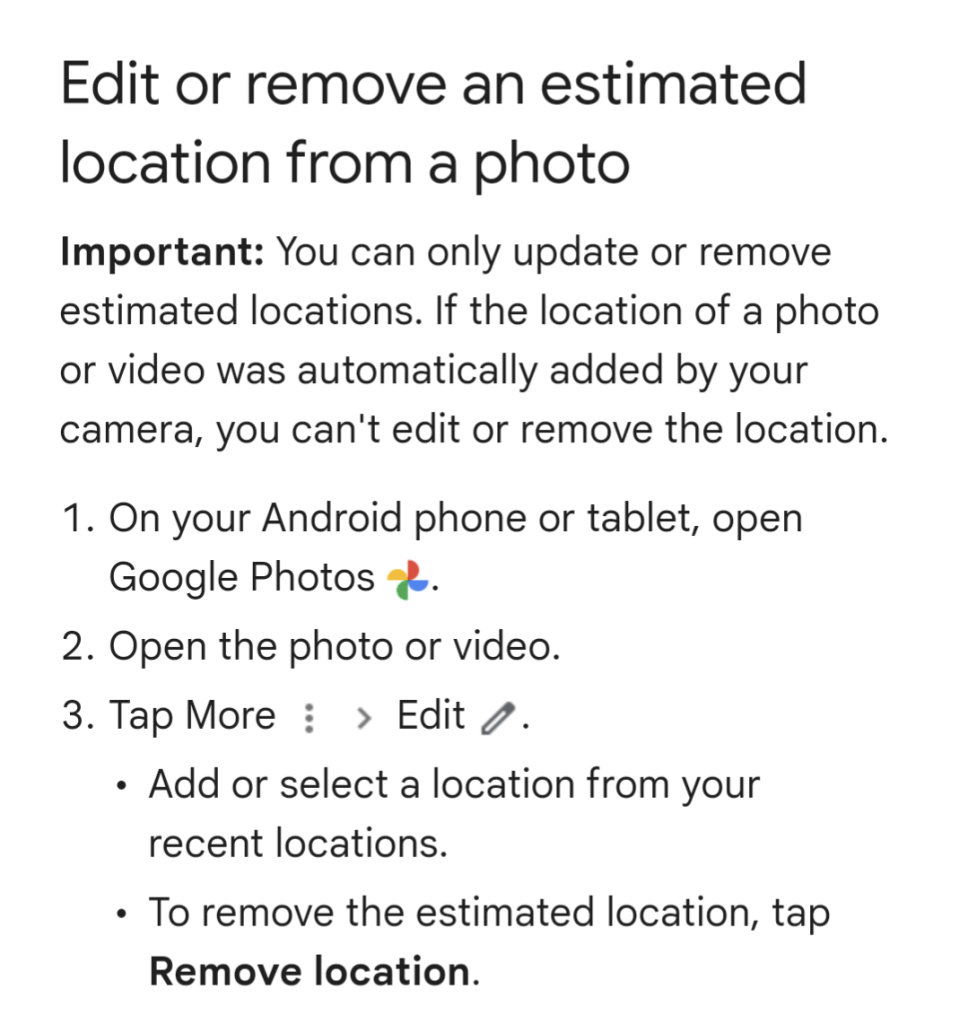
Obviously, accurate location data on photos is more useful to a data mining operation like Google.
From Google: "Important: You can only update or remove estimated locations. If the location of a photo or video was automatically added by your camera, you can't edit or remove the location."
It's enshitification in action.
Source: https://support.google.com/photos/answer/6153599?hl=en&sjid=8103501961576262529-AP
#technology #tech @technology #business #enshitification #Android #Google @pluralistic #infosec










 Credit:
Credit:  Credit:
Credit:  (Art by
(Art by  (Art by
(Art by