Search
Items tagged with: infosec
I was asked by a journalist to answer a bunch of supply chain security questions today and I have to say, I am just a bit exasperated at this point.
Nothing wrong with the questions, but the expectation that there is a template for how you assess risk for your business or a protocol you need to follow is deeply frustrating.
Knowing how your business works and what data you must protect is your job. No one else can figure this out for you. There isn't a service, a survey, or a AI agent that can do this for you.
Risk management is hard. In a field that changes at the pace of #InfoSec it often feels impossible, but looking for shortcuts or copying your friends answers isn't going to get the job done.
Dedication, diligence and determination are the way forward.
Hello FediFriends. We forgot to do socials for this week's podcast!
Let's fix that. @0xBennyV and @chetwisniewski discussed Wannacry this week. Can you believe that it has been 8 years already? Seems like it was only yesterday we watched some of the world's largest transportation companies succumb to "ransomware" and then it was accidentally thwarted by someone who claimed to be a security researcher, but was actually a malware author. What a peculiar story this one was...
Our latest episode is now live! We cover the LulzSec hacking spree from 2011, and boy was it a busy 50 days for the 6 core hackers. All but one were ultimately caught, but it is a sprawling and occasionally humourous story. @chetwisniewski was even indirectly involved and shared his thoughts with the BBC on the day their rampage ended (https://www.youtube.com/watch?v=AupFf80ZWhw)
Listen now: https://securitytaketwo.com/lulzsec/
#InfoSec #LulzSec #Hacktivism @0xBennyV

Kasia Madera speaking to Chester Wisniewski, from the internet security firm Sophos, on hacking
Kasia Madera speaking to Chester Wisniewski, from the internet security firm Sophos, on hacking on Monday 27th June 2011YouTube
Microsoft Copilot for SharePoint just made recon a whole lot easier. 🚨
One of our Red Teamers came across a massive SharePoint, too much to explore manually. So, with some careful prompting, they asked Copilot to do the heavy lifting...
It opened the door to credentials, internal docs, and more.
All without triggering access logs or alerts.
Copilot is being rolled out across Microsoft 365 environments, often without teams realising Default Agents are already active.
That’s a problem.
Jack, our Head of Red Team, breaks it down in our latest blog post, including what you can do to prevent it from happening in your environment.
📌Read it here: https://www.pentestpartners.com/security-blog/exploiting-copilot-ai-for-sharepoint/
#RedTeam #OffSec #AIsecurity #Microsoft365 #SharePoint #MicrosoftCopilot #InfoSec #CloudSecurity
Exploiting Copilot AI for SharePoint | Pen Test Partners
TL;DR AI Assistants are becoming far more common Copilot for SharePoint is Microsoft’s answer to generative AI assistance on SharePoint Attackers will look to exploit anything they can get their hands on Your current controls and logging may be insuf…Jack Barradell-Johns (Pen Test Partners)
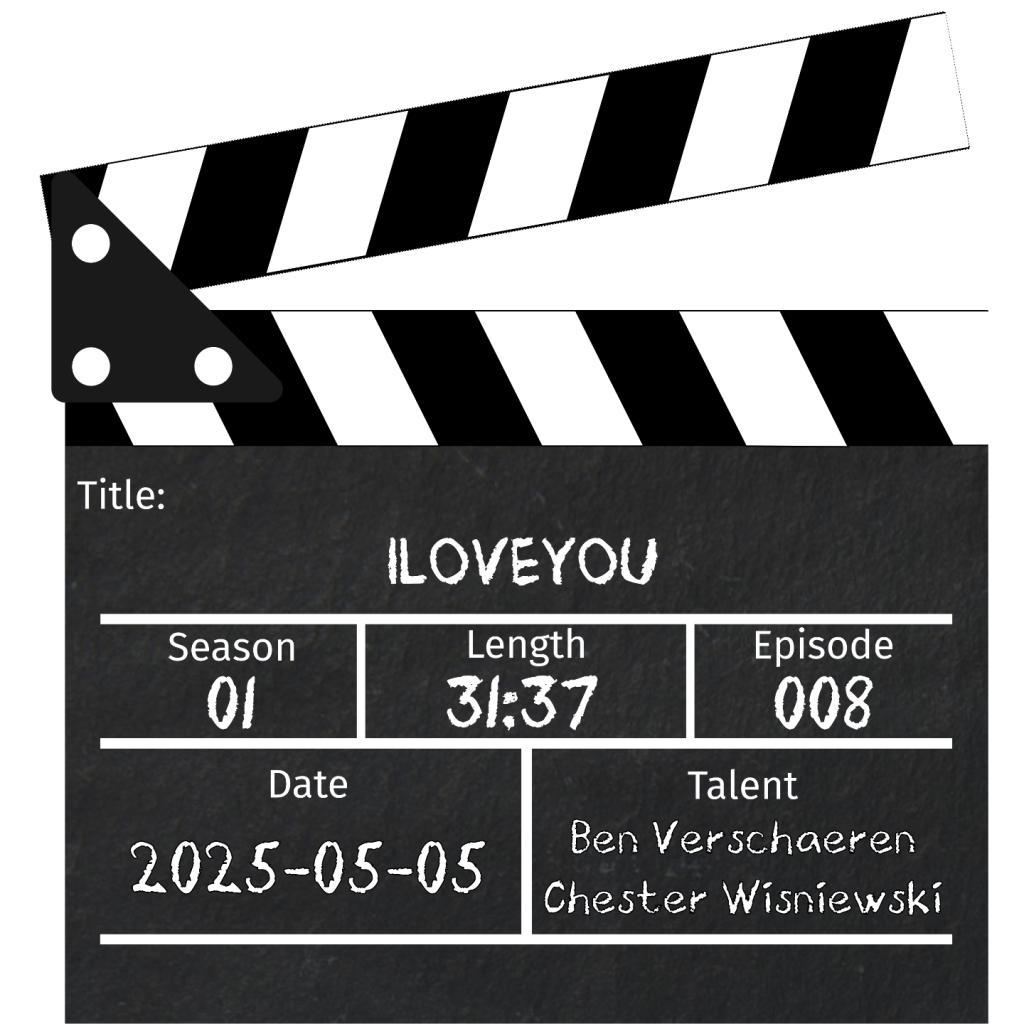
Today's the day. May 4, 2000 the ILOVEYOU worm took the world by storm. @0xBennyV and @chetwisniewski have all the gory details of this milestone event in computer security history 25 years on.
https://securitytaketwo.com/iloveyou/
#InfoSec #Podcast #ILOVEYOU
Excellent news! Episode 7 is now online and available in all your favourite podplaces. @chetwisniewski and @0xBennyV discuss the many Uber breaches and cover off some of the different errors that lead to their being compromised at least 5 times (that we know of!).
FreeTube ─ Watch YouTube without ads, without login, and with private playlists.
#google #YouTube #privacy #ad #safety #security #InfoSec #data #advertisement #tech #technology #BigTech #app #apps #tip #tips
FreeTube - The Private YouTube Client
FreeTube is a feature-rich and user-friendly YouTube client with a focus on privacy.freetubeapp.io
Our next episode is now live! Learn about our insights and takeaways from the Transport for London hack in September 2024. Your daily reminder that every attack need not be a ransomware attack...
#Podcast #InfoSec
https://securitytaketwo.com/transportforlondon/
Transport for London
Security Take(s) Two - Transport for LondonSecurity Take Two - Real. Serious. Security.
Update Signal and pay attention when joining groups:
https://www.wired.com/story/russia-signal-qr-code-phishing-attack/
👉 No, Signal has not been compromised
👉 No, Signal encryption has not been broken
👉 No, there is no back-door in Signal
You should continue using Signal. The update is responding to a sophisticated, state-level attack targeting specific groups.
Unless you are a high-value target, you are almost certainly never going to see this in the wild.
If you know you are a high-value target, ask your support.

A Signal Update Fends Off a Phishing Technique Used in Russian Espionage
Google warns that hackers tied to Russia are tricking Ukrainian soldiers with fake QR codes for Signal group invites that let spies steal their messages. Signal has pushed out new safeguards.Andy Greenberg (WIRED)
There's a "Signal deanonymized" thing going around:
https://gist.github.com/hackermondev/45a3cdfa52246f1d1201c1e8cdef6117
Stay calm. Deep breaths.
👉 while this is a real consideration, the only thing the attacker gets from this is a very rough (kilometers or tens of kilometers radius) location
👉 other communication platforms that use any kind of caching CDN to deliver attachments are just as affected
👉 you almost certainly should continue to use Signal, unless you specifically know that this is a big problem for you.

Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platform
Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platform - research.mdGist
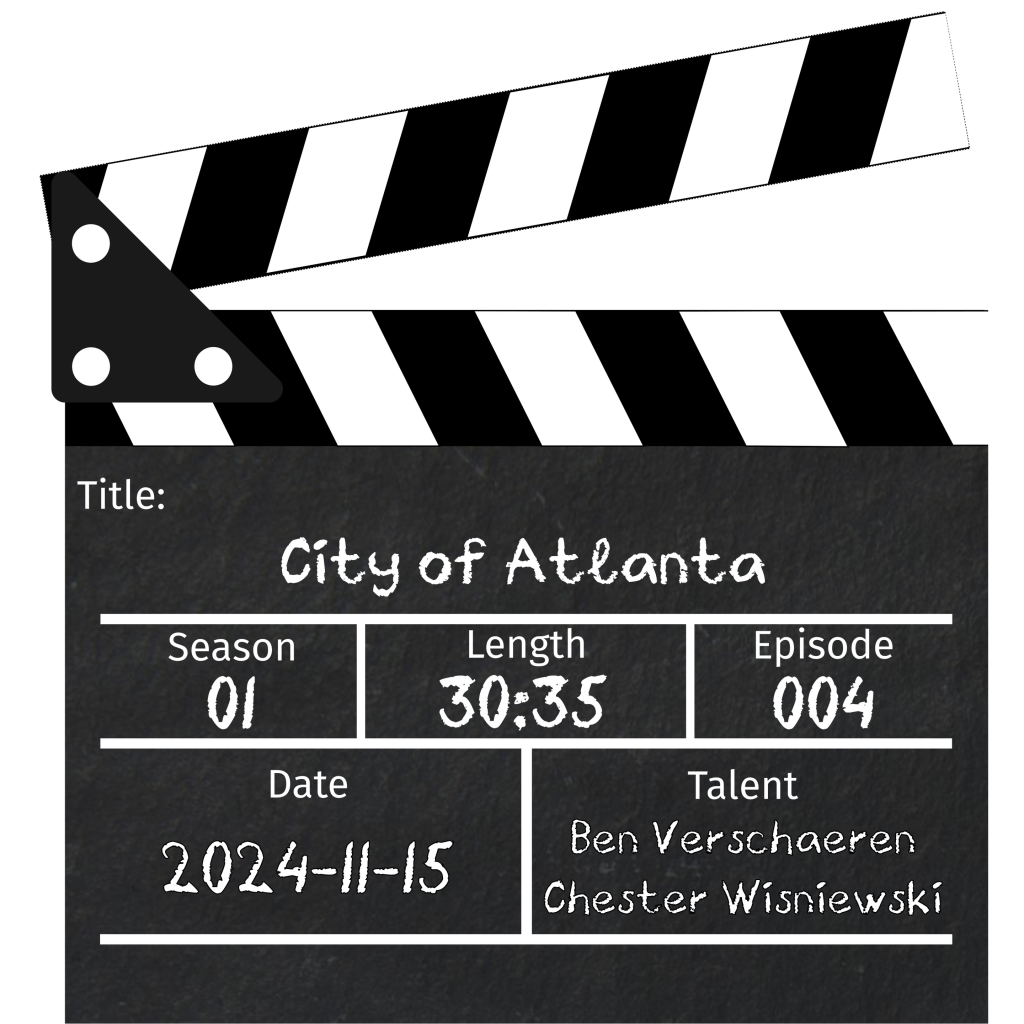
City of Atlanta
When the City of Atlanta was hit by the ransomware group SamSam in 2018 it made headlines worldwide. Headlines often cited costs ranging from $2.Security Take Two - Real. Serious. Security.
Since it's Halloween...
The Malware Mash!
https://thecyberwire.com/stories/79cb0c1f7ff74f638c54fddeaa6177ae/the-malware-mash

The Malware Mash
Happy Halloween from the team at N2K Networks! We hope you will join us in our Halloween tradition of listening to the Malware Mash.The CyberWire Staff (The CyberWire)
Krótko i treściwie, dlaczego warto używać Signala i jak go zainstalować (nadaje się do podsyłania mniej technicznym znajomym, których chcemy przekonać do jedynego słusznego komunikatora 😉)
https://www.youtube.com/watch?v=iwB_zC51KlY
PS. Czy można jeszcze liczyć na jakąś instancję Invidious, czy YouTube pokonał już wszystkie?
@signalapp @mateuszchrobok #infosec #cyberbezpieczenstwo #signal

Signal - komunikator, z którym możesz czuć się bezpiecznie
Proponuję Ci korzystanie z Signala, jednego z najlepszych, chociaż nie najpopularniejszych komunikatorów. Dlaczego? Ponieważ w bezpiecznej komunikacji nie ch...YouTube
I have a friend who is being harassed and threatened semi-anonymously via Facebook. She knows *who* it is, but Facebook and Police are characteristically being uselss.
I am kinda useless at this side of deanonymization, but does anyone have advice or resources for deanonymizing enough to get cops to move?
Reminder: As we approach Cybersecurity Awareness Month (Do not abbreviate) we need to not go down the rabbit hole when providing advice to our friends, family, and the media.
People are only likely to pay attention to personal computer security for maybe 2 minutes a year. Don't hype threats that aren't there (Public WiFi, Juice Jacking, Gen AI threats), focus on the basics that are causing most of the harm... Patch your iPhone/Android/PC/Mac/Router and use a password manager.
Ok, here's the deal on the "YubiKey cloning attack" stuff:
:eyes_opposite: Yes, a way to recover private keys from #YubiKey 5 has been found by researchers.
But the attack *requires*:
👉 *physically opening the YubiKey enclosure*
👉 physical access to the YubiKey *while it is authenticating*
👉 non-trivial electronics lab equipment
I cannot stress this enough:
✨ In basically every possible scenario you are safer using a YubiKey or a similar device, than not using one. ✨
Pleased to announce the launch of Surveillance Watch, an interactive map and resource that documents the hidden connections within the opaque surveillance industry: https://www.surveillancewatch.io/
By mapping out the intricate web of surveillance companies, their subsidiaries, partners, and financial backers, we hope to expose the enablers fueling this industry's extensive rights violations, ensuring they cannot evade accountability for being complicit in this abuse.
#Privacy #Surveillance #InfoSec
Surveillance Watch: They Know Who You Are
Surveillance Watch is an interactive map revealing the intricate connections between surveillance companies, their funding sources and affiliations.Surveillance Watch
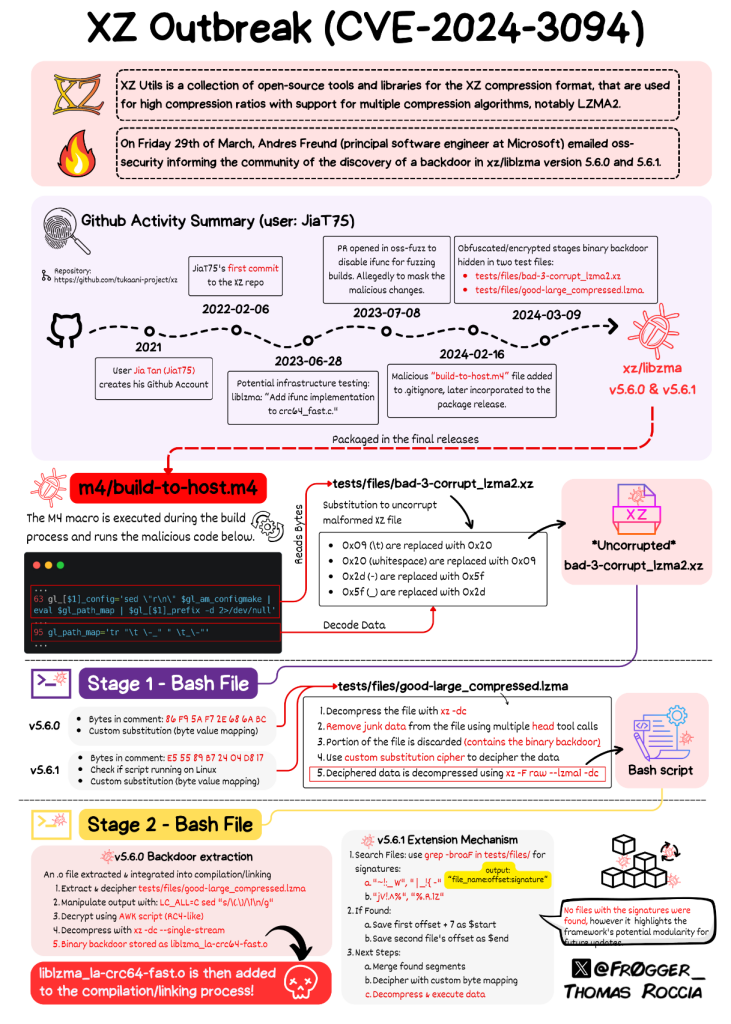
That backdoor in sshd (via xz / liblzma) affects recent versions of Kali Linux:
Kali Linux announced that the impact of this vulnerability affected Kali between March 26th and March 29th. If you updated your Kali installation on or after March 26th, applying the latest updates today is crucial to address this issue. However, if you did not update your Kali installation before the 26th, you are not affected by this backdoor vulnerability.
More info here:
https://infosec.exchange/@kalilinux/112180505434870941
A couple things to think about here:
This appears to be a malicious maintainer - not a compromised account. Meaning the person themselves, coded this in an pushed it out.
So:
1) Did they try and backdoor any other code?
2) Are they part of a greater campaign or is anyone else helping them.
This is a massive breach of trust.
That said! Huge kudos to Andres Freund, Florian Weimer, and others in finding this.
A lot of eyes are on this now. CISA is involved. Major distros are involved, etc. Many eyes and such.

Beware! Backdoor found in XZ utilities used by many Linux distros (CVE-2024-3094) - Help Net Security
A vulnerability (CVE-2024-3094) in XZ Utils may enable a malicious actor to gain unauthorized access to Linux systems remotely.Zeljka Zorz (Help Net Security)
When interviewing a man and woman together, I will often deliberately give the woman the last word. I'm not overt about it, I simply structure the conversation that way.
I've noticed that quite often the man will then jump in with, "one more thing," he wants to share.
Men — don't do this!
Ladies, I'm wondering how often this sort of thing happens to you. I'm guessing it's common, but I'm also aware my perception might be skewed by my own annoyance by it.
If you don’t use a password manager, what’s the reason?
Feel free to comment.
Reposts appreciated for more reach.
- Don't know how to use it (18%, 21 votes)
- Don't trust it (77%, 90 votes)
- Don't know what it is (4%, 5 votes)
The endgame is almost always #spam. LI accounts frequently have complete copies of their owners' professional address books, a valuable set of mostly high-quality addresses.
Very rarely (all day every day, but only to a tiny percentage of people) they are going after the account owner specifically or hitting contacts of their primary target to impersonate them.
I'm positively impressed by the latest shame scam I just received. It even includes a password of mine that has been reported as part of a dump several years ago, and it makes the claim that they somehow installed a trojan virus on all my devices and caught me on camera masturbating way more impactful.
I wanted to congratulate them for the marginal ingenuity but unfortunately they do indicate it's useless to reply directly to the sender email address. 😞
Fundacja IT Girls przygotowała e-booka "Bezpieczni online - twój klik ma znaczenie", warto się zapoznać
https://sklep.itgirls.org.pl/e-book-bezpieczni-online-twoj-klik-ma-znaczenie/
(pobranie za darmo wymaga podania imienia, nazwiska i adresu e-mail)
... what. the. fuck. " https://www.bleepingcomputer.com/news/security/keepass-exploit-helps-retrieve-cleartext-master-password-fix-coming-soon/
#infosec #cybersecurity #passwordmanagers

KeePass exploit helps retrieve cleartext master password, fix coming soon
The popular KeePass password manager is vulnerable to extracting the master password from the application's memory, allowing attackers who compromise a device to retrieve the password even with the database is locked.Bill Toulas (BleepingComputer)
You may not reuse any of the most recent 12 faces.
#infosec #PasswordExpiration #BYOD
#OpenSource #FreeSoftware #privacy #security #infosec
🤡 #1Password becomes #spyware:
https://blog.1password.com/privacy-preserving-app-telemetry/

We're changing how we discover and prioritize improvements | 1Password
Learn about a new, privacy-preserving in-app telemetry system that 1Password is trialing with its employees.1Password