Search
Items tagged with: hacking
💻🌍 Digital sovereignty might sound big — but it’s really about taking control of the tech that shapes our lives. It’s important for young people to learn that technology doesn’t have to be a black box — it’s something you can understand, explore, and even build yourself!
That’s why I love  @fsfe’s "Youth Hacking 4 Freedom" — a coding competition for teens (14–18) across Europe. The next round kicks off on January 1, 2026 🚀
@fsfe’s "Youth Hacking 4 Freedom" — a coding competition for teens (14–18) across Europe. The next round kicks off on January 1, 2026 🚀
If you’re into coding, creativity, and shaping the digital future, this is your chance to shine!
Jump right away to the registration: https://yh4f.org/register
Or learn more about it: https://yh4f.org
#FreeSoftware #softwareFreedom #hacking #programming #yh4f #fsfe #digitalSovereignty #teens
Youth Hacking 4 Freedom - FSFE
If you like programming, tinkering, having fun with software and if you are up for a challenge, we have something exciting for you: "Youth Hacking 4 Freedo...FSFE - Free Software Foundation Europe
Remembering Chiptunes, the Demoscene and the Illegal Music of Keygens
We loved keygens back in the day. Our lawyers advise us to clarify that that’s all because of the demo-scene style music embedded in them, not because we used them …read more
#hacking #projects
https://hackaday.com/2025/07/20/remembering-chiptunes-the-demoscene-and-the-illegal-music-of-keygens/
Remembering Chiptunes, The Demoscene And The Illegal Music Of Keygens
We loved keygens back in the day. Our lawyers advise us to clarify that it’s because of the demo-scene style music embedded in them, not because we used them for piracy. [Patch] must feel the…Hackaday
38C3: Lawsuits are Temporary; Glory is Forever
One of the blockbuster talks at last year’s Chaos Communications Congress covered how a group of hackers discovered code that allegedly bricked public trains in Poland when they went into …read more
#hacking #projects
https://hackaday.com/2024/12/29/38c3-lawsuits-are-temporary-glory-is-forever/
38C3: Lawsuits Are Temporary; Glory Is Forever
One of the blockbuster talks at last year’s Chaos Communications Congress covered how a group of hackers discovered code that allegedly bricked public trains in Poland when they went into ser…Hackaday
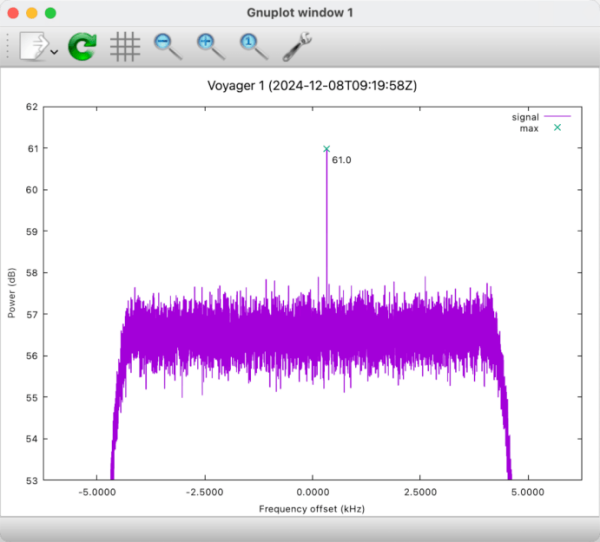
Amateur Radio Operators Detect Signals from Voyager 1
At the time of its construction in the 1950s, the Dwingeloo Radio Observatory was the largest rotatable telescope in the world with a dish diameter of 25 meters. It was …read more
#hacking #projects
https://hackaday.com/2024/12/11/amateur-radio-operators-detect-signals-from-voyager-1/
Amateur Radio Operators Detect Signals From Voyager 1
At the time of its construction in the 1950s, the Dwingeloo Radio Observatory was the largest rotatable telescope in the world with a dish diameter of 25 meters. It was quickly overtaken in the ran…Hackaday
3D Space Can Be Tiled With Corner-free Shapes
Tiling a space with a repeated pattern that has no gaps or overlaps (a structure known as a tessellation) is what led mathematician [Gábor Domokos] to ponder a question: how …read more
#hacking #projects
https://hackaday.com/2024/11/23/3d-space-can-be-tiled-with-corner-free-shapes/
3D Space Can Be Tiled With Corner-free Shapes
Tiling a space with a repeated pattern that has no gaps or overlaps (a structure known as a tessellation) is what led mathematician [Gábor Domokos] to ponder a question: how few corners can a shape…Hackaday
StratoSoar Glider Flies Itself from High Altitude
As the technology available to the average hacker and maker gets better and cheaper each year, projects which at one time might have only been within the reach of government …read more
#hacking #projects
https://hackaday.com/2024/09/23/stratosoar-glider-flies-itself-from-high-altitude/
StratoSoar Glider Flies Itself From High Altitude
As the technology available to the average hacker and maker gets better and cheaper each year, projects which at one time might have only been within the reach of government agencies are inching cl…Hackaday
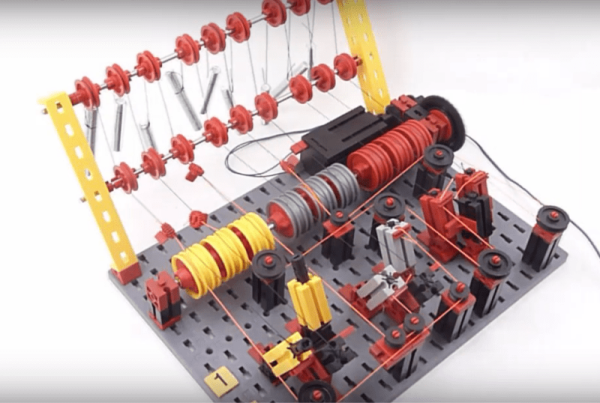
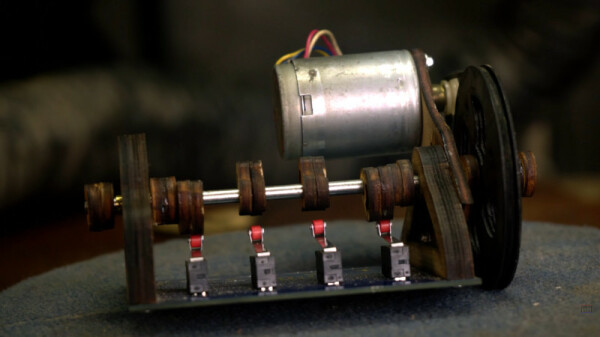
Mechanical Logic Gates With Amplification
One of the hardest things about studying electricity, and by extension electronics, is that you generally can’t touch or see anything directly, and if you can you’re generally having a …read more
#hacking #projects
https://hackaday.com/2024/09/20/mechanical-logic-gates-with-amplification/
The Trashiest Of Mains Inverters
Switch-mode technology has made inverters which take a low DC voltage and turn it into a usable mains voltage within the reach of everybody. But still, there might be moments …read more
#hacking #projects
https://hackaday.com/2024/08/31/the-trashiest-of-mains-inverters/
The Trashiest Of Mains Inverters
Switch-mode technology has made inverters which take a low DC voltage and turn it into a usable mains voltage within the reach of everybody. But still, there might be moments when a mains supply is…Hackaday
MIDI Controller in a Cubic Inch
MIDI as a standard has opened up a huge world to any musician willing to use a computer to generate or enhance their playing and recording. Since the 80s, it …read more
#hacking #projects
https://hackaday.com/2024/07/27/midi-controller-in-a-cubic-inch/
MIDI Controller In A Cubic Inch
MIDI as a standard has opened up a huge world to any musician willing to use a computer to generate or enhance their playing and recording. Since the 80s, it has it has revolutionized the way music…Hackaday
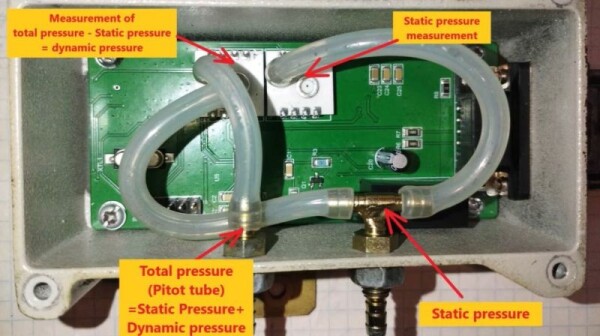
Reverse-Engineering a Shahed-136 Drone Air Data Computer
An air data computer (ADC) is a crucial part of an avionics package that can calculate the altitude, vertical speed, air speed and more from pressure (via pitot tubes) and …read more
#hacking #projects
https://hackaday.com/2024/07/15/reverse-engineering-a-shahed-136-drone-air-data-computer/
Reverse-Engineering A Shahed-136 Drone Air Data Computer
An air data computer (ADC) is a crucial part of an avionics package that can calculate the altitude, vertical speed, air speed and more from pressure (via pitot tubes) and temperature inputs. When …Hackaday
That backdoor in sshd (via xz / liblzma) affects recent versions of Kali Linux:
Kali Linux announced that the impact of this vulnerability affected Kali between March 26th and March 29th. If you updated your Kali installation on or after March 26th, applying the latest updates today is crucial to address this issue. However, if you did not update your Kali installation before the 26th, you are not affected by this backdoor vulnerability.
More info here:
https://infosec.exchange/@kalilinux/112180505434870941
A couple things to think about here:
This appears to be a malicious maintainer - not a compromised account. Meaning the person themselves, coded this in an pushed it out.
So:
1) Did they try and backdoor any other code?
2) Are they part of a greater campaign or is anyone else helping them.
This is a massive breach of trust.
That said! Huge kudos to Andres Freund, Florian Weimer, and others in finding this.
A lot of eyes are on this now. CISA is involved. Major distros are involved, etc. Many eyes and such.

Beware! Backdoor found in XZ utilities used by many Linux distros (CVE-2024-3094) - Help Net Security
A vulnerability (CVE-2024-3094) in XZ Utils may enable a malicious actor to gain unauthorized access to Linux systems remotely.Zeljka Zorz (Help Net Security)
There’s Hope For That Cheap Lathe Yet!
There may be few cases where the maxim that “you get what you pay for” rings true, than a lathe. The less you spend on a lathe, the closer you …read more
#hacking #projects
https://hackaday.com/2024/02/25/theres-hope-for-that-cheap-lathe-yet/
There’s Hope For That Cheap Lathe Yet!
There may be few cases where the maxim that “you get what you pay for” rings true, than a lathe. The less you spend on a lathe, the closer you get to a lathe-shaped object and the furth…Hackaday
Hacking a Philips toothbrush head to allow you to use it beyond its normal lifetime. Yes, the toothbrush _head_ is hackable. This is a fantastic tale of reverse engineering. Be sure to read the followup at the bottom of the article.
https://kuenzi.dev/toothbrush/
#hacking #reverseengineering #sdr
Hacking my “smart” toothbrush
After buying a new Philips Sonicare toothbrush I was surprised to see that it reacts to the insertion of a brush head by blinking an LED.ckuenzi (The Twenty Percent)
Territories across the northern hemisphere are suffering through record-breaking heatwaves this summer. Climate scientists are publishing graphs with red lines jagging dangerously upwards as unprecedented numbers pour in. Residents of …read more
#hacking #projects
https://hackaday.com/2023/07/27/how-to-survive-a-wet-bulb-event/
How To Survive A Wet Bulb Event
Territories across the northern hemisphere are suffering through record-breaking heatwaves this summer. Climate scientists are publishing graphs with red lines jagging dangerously upwards as unprec…Hackaday
[Jeff Geerling] has tried building his own network-attached storage before, but found that the Raspberry Pi just wasn’t able to keep pace with his demands. He’s back with a new …read more
#hacking #projects
https://hackaday.com/2023/07/20/diy-all-flash-nas-vs-commercial-hardware/
DIY All-Flash NAS Vs. Commercial Hardware
[Jeff Geerling] has tried building his own network-attached storage before, but found that the Raspberry Pi just wasn’t able to keep pace with his demands. He’s back with a new all-flas…Hackaday
The hacker also stole an encryption key for a portion of the encrypted backups by accessing a cloud storage database shared by both LastPass and GoTo.
#news #tech #technology #security #privacy #Lastpass #breach #hacking
https://www.pcmag.com/news/lastpass-sibling-company-goto-loses-encrypted-backups-to-hackers
https://www.techdirt.com/2022/12/05/law-enforcement-is-extracting-tons-of-data-from-vehicle-infotainment-systems/
#infotainment #databrokers #siriusxm #hacking #privacy #cars #1

Law Enforcement Is Extracting Tons Of Data From Vehicle Infotainment Systems
For years, cars have collected massive amounts of data. And for years, this data has been extraordinarily leaky. Manufacturers don’t like to discuss how much data gets phoned home from vehicl…Techdirt
After completing a thorough investigation, we found that he has not been hacked. Unfortunately, that's just how he is.
#Cyber #CyberSecurity #SocialEngineering #hacking