Search
Items tagged with: security
#meme #politics #pedophile #abuse #children #security #system #matrix #trump #government #tax #taxes #finance #money #elite #whitehouse #president #politician #democracy #evil #fail #worldorder #world #maga #qanon #conspiracy #future #view #apocalypse #doomsday
Firefox's AI Kill Switch is a Trap: How Mozilla Made AI Your Problem
"Mozilla recently released AI controls for Firefox. On the surface, this sounds like a win for user choice in an era of AI-everything.
If we dig deeper, you can start to see that the kill switch isn’t the whole story. This feature acts like an accountability sink…"
#mozilla #firefox #tech #technology #info #BigTech #browser #internet #safety #security #InfoSec #AI #ArtificialIntelligence #Fuck_AI
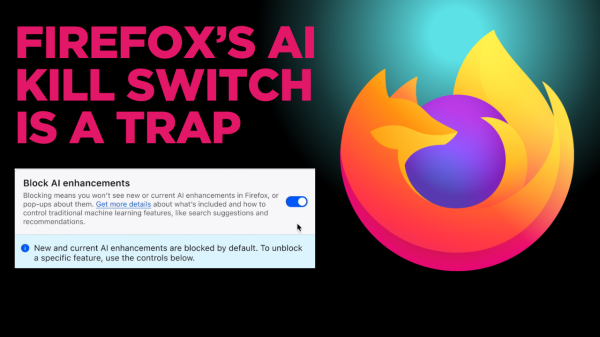
Firefox’s AI Kill Switch is a Trap: How Mozilla Made AI Your Problem
TL;DR: Mozilla recently released AI controls for Firefox: a single control panel that lets people disable AI features in the browser or pick and choose which to leave on.Youssuff Quips
Tell #UK Government: Protect #VPN use in the UK - Open Rights Group
VPNs help people to stay #private and #safe #online. However, the Government, wants to force us to verify our age when we buy a VPN effectively deterring many people from using them.
Sign the #petition to protect the use of VPNs, so that people can stay safe and #secure online.
https://action.openrightsgroup.org/tell-government-protect-vpn-use-uk
#authoritarianism #ToxicLabour #BigBrother #security #digital #surveillance

Tell the Government: Protect VPN use in the UK
Take action! Protect VPN use in the UK VPNs help people to stay private and safe online. Young people use them to avoid harassment, or protect location data. Companies use them to make sure remote log-in to their networks are secure.Open Rights Group
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: https://notepad-plus-plus.org/news/hijacked-incident-info-update/
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software

Extending Kernel Race Windows Using '/dev/shm'
Recently, I came across this kernelCTF submission where the author mentions a novel technique for extending race windows in the Linux kernel: I learned…faith2dxy.xyz
WhatsApp Vulnerability Exposes 3.5 Billion Users' Phone Numbers
https://cybersecuritynews.com/whatsapp-vulnerability-exposes-3-5-billion-users/
#GAFAM #WhatsApp #Security #Privacy

WhatsApp Vulnerability Exposes 3.5 Billion Users' Phone Numbers
A critical security flaw in WhatsApp has allowed researchers to expose the phone numbers of 3.5 billion users, marking one of the most significant data leaks ever documented.Guru Baran (CybersecurityNews)
Something that’s been bothering me for years in the security world: why do researchers demand bug bounties for vulnerabilities in open source projects, when the very contributors maintaining and fixing those issues get nothing, just goodwill?
It feels deeply unfair. The burden falls on unpaid maintainers, yet bounty hunters get rewarded. If you want a paid bounty, maybe help fund the people who actually fix the mess too.
GrapheneOS version 2025061000 released:
https://grapheneos.org/releases#2025061000
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/23046-grapheneos-version-2025061000-released
#GrapheneOS #privacy #security
GrapheneOS releases
Official releases of GrapheneOS, a security and privacy focused mobile OS with Android app compatibility.GrapheneOS
**Backdoor Campaign Affecting Thousands of ASUS Routers**
https://www.greynoise.io/blog/stealthy-backdoor-campaign-affecting-asus-routers
**#asus #security #backdoor #malware**

GreyNoise Discovers Stealthy Backdoor Campaign Affecting Thousands of ASUS Routers
GreyNoise uncovers a stealth campaign exploiting ASUS routers, enabling persistent backdoor access via CVE-2023-39780 and unpatched techniques.www.greynoise.io
PSA: The Tor Browser Security Level slider cannot be relied upon without a full browser restart (per an anonymous community report and confirmed by Privacy Guides staff) - Make sure you are aware of this if you rely on this feature for your safety.
https://www.privacyguides.org/articles/2025/05/02/tor-security-slider-flaw/
#TorBrowser #Security #MullvadBrowser #Privacy #PrivacyGuides #Article
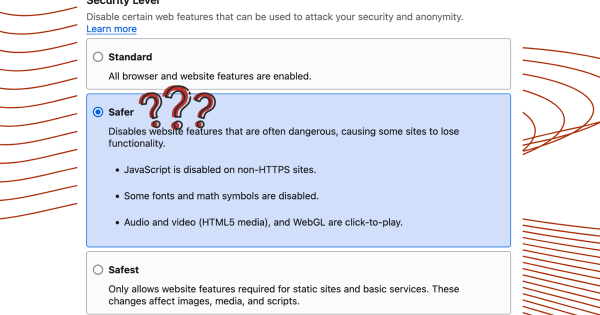
A Flaw With the Security Level Slider in Tor Browser
PSA: The security level slider in Tor Browser (and Mullvad Browser) does not fully apply until restarting the browser.www.privacyguides.org
New Privacy Guides video 📺✨
by @jw
If you've wondered about
the difference between:
Privacy,
Security,
and Anonymity 
And why some privacy-focused
services are worth using even when they don't provide perfect anonymity, watch this!
It's truly an amazing short video!
Everyone should watch it 👇
https://www.privacyguides.org/videos/2025/03/14/stop-confusing-privacy-anonymity-and-security/
#PrivacyGuides #Privacy #Security #Anonymity

Stop Confusing Privacy, Anonymity, and Security
Are you mixing up privacy, security, and anonymity? Don't worry, it's more common than you might think! In this week's video we break down each term, so you can make educated decisions on what tools are best for you.www.privacyguides.org
FreeTube ─ Watch YouTube without ads, without login, and with private playlists.
#google #YouTube #privacy #ad #safety #security #InfoSec #data #advertisement #tech #technology #BigTech #app #apps #tip #tips
FreeTube - The Private YouTube Client
FreeTube is a feature-rich and user-friendly YouTube client with a focus on privacy.freetubeapp.io
https://frederikbraun.de/home-assistant-can-not-be-secured-for-internet-access.html
https://thecopenhagenbook.com/
🔴 Agenda na #JesienLinuksowa już dostępna! 🔴
W programie: #DevOps, #security, #gaming, #prywatność i więcej!
Goście specjalni: Kuba Mrugalski (@uwteam), Tomasz Zieliński (@infzakladowy)
Dodatkowo: 💬 Unconference ⚡ Lightning Talks 🎉 Fedora release party!
Do zobaczenia! 🥳
Do you want to help make software safer? Find the bugs in our ntpd-rs!
The ntpd-rs Bug Bounty Program offers a reward to anyone who finds a qualifying vulnerability.
Read the details here: https://yeswehack.com/programs/pendulum-bug-bounty-program
This Bug Bounty Program is organized and funded by @sovtechfund . Read more about this initiative here: https://www.sovereigntechfund.de/programs/bug-resilience/

ntpd-rs Bug Bounty Program bug bounty program - YesWeHack
ntpd-rs Bug Bounty Program bug bounty program detailsYesWeHack #1 Bug Bounty Platform in Europe
So now that we all understand that thanklessly relying on free work of overworked maintainers is a problem, how about we put our money where our mouth is?
I think @AndresFreundTec needs a fat bonus check for saving our asses.
And Lasse Collin needs a lot of support, and probably a nice vacation.
I pledge $100, for starters.
Now how can we make sure to send the funds to the correct people?
Or is there already any fundraiser that I missed?
„GitHub Disables The XZ Repository Following Today's Malicious Disclosure“
https://www.phoronix.com/news/GitHub-Disables-XZ-Repo

GitHub Disables The XZ Repository Following Today's Malicious Disclosure
Today's disclosure of XZ upstream release packages containing malicious code to compromise remote SSH access has certainly been an Easter weekend surprise..www.phoronix.com
Millions Of #google #whatsapp #Facebook #2FA #Security Codes #Leak Online
Security experts advise against using SMS messages for two-factor authentication codes due to their vulnerability to interception or compromise. Recently, a security researcher discovered an unsecured database on the internet containing millions of such codes, which could be easily accessed by anyone.
#news #tech #technews #technology #privacy

Millions Of Google, WhatsApp, Facebook 2FA Security Codes Leak Online
A security researcher has discovered an unsecured database on the internet containing millions of two-factor authentication security codes. Here's what you need to know.Davey Winder (Forbes)
Y'all know not to use #Temu right? Right???
Temu app contains ‘most dangerous’ #spyware in circulation: class action lawsuit | Fashion Dive
https://www.fashiondive.com/news/temu-class-action-lawsuit-data-collection/699328/

Temu app contains ‘most dangerous’ spyware in circulation: class action lawsuit
The complaint alleges that the fast fashion giant gains access to “literally everything on your phone” once its app is downloaded.Fashion Dive
But to be fair ...
Is it the implementation language being the main issue? Or is it the flexibility of extending it with plugins and that it is effectively a setuid tool, granting root access immediately when an unprivileged user starts the program (the privileges are reduced first when it has parsed the sudo config).
Sudo is a nice tool from the user's side. But security wise it's a disastrous approach. Privileges should first be elevated *after* the config has been parsed and the expected privilege level has been established. Then the tool should ideally jump to that privilege level directly.
This post introduces some new ideas ... https://tim.siosm.fr/blog/2023/12/19/ssh-over-unix-socket/
It's not a perfect approach in all cases. But it gets rid of the setuid issue.
sudo without a setuid binary or SSH over a UNIX socket
In this post, I will detail how to replace sudo (a setuid binary) by using SSH over a local UNIX socket. I am of the opinion that setuid/setgid binaries are a UNIX legacy that should be deprecated.Siosm's blog
Seriously, WTF @protonmail ?
#YouHadOneJob as #eMail #Provider and that is to get shit reliably sent and recieved.
If that's too hard then how should anyone trust them re: #security and #privacy?
Spoiler: Noine should!
https://www.youtube.com/watch?v=QCx_G_R0UmQ

ProtonMail Sends User IP and Device Info to Swiss Authorities.
Original articleshttps://mobile.twitter.com/tenacioustek/status/1434604102676271106https://techcrunch.com/2021/09/06/protonmail-logged-ip-address-of-french-a...YouTube
#BraveBrowser is installing VPNs without users' consent, even if you didn't willingly enable their #VPN service. Just stop using #Brave, it's garbage.
Edit: the services are disabled by default, but they were still installed with very little to no transparency about them towards the user, alongside all the other stuff that's often unwanted from Brave users (Pocket on Firefox is to blame too, lol.)
https://www.ghacks.net/2023/10/18/brave-is-installing-vpn-services-without-user-consent/
#Browser #Security #Privacy #OpenSource #FreeSoftware #LibreSoftware

Are your Google Docs safe from AI training?
With AI continuing its slow rise to prominence, consumers are concerned their personal content is being used to train Google's generative service.Jack Wallen (ZDNET)
https://lapcatsoftware.com/articles/2023/7/1.html
#security #privacy #firefox #wtf
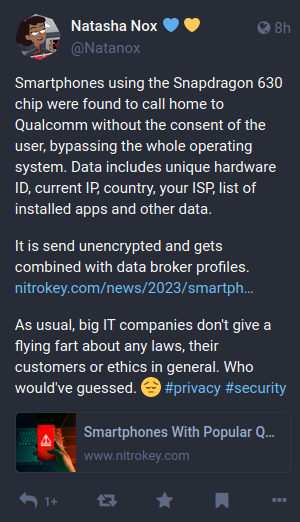
Smartphones using the Snapdragon 630 chip were found to call home to Qualcomm without the consent of the user, bypassing the whole operating system. […]
< SEE ATTACHMENT >
EDIT / UPDATE:
Martijn Braam took a look and provides a valuable counterstatement. Thx @bart
https://blog.brixit.nl/nitrokey-dissapoints-me/
Still without the actual data that gets transmitted though. Unless someone does it first I'll replicate the test setup myself tomorrow and post my findings here.
#privacy #security
#OpenSource #FreeSoftware #privacy #security #infosec
🤡 #1Password becomes #spyware:
https://blog.1password.com/privacy-preserving-app-telemetry/

We're changing how we discover and prioritize improvements | 1Password
Learn about a new, privacy-preserving in-app telemetry system that 1Password is trialing with its employees.1Password
https://www.bleepingcomputer.com/news/security/us-sues-google-for-abusing-dominance-over-online-ad-market/
#Security

U.S. sues Google for abusing dominance over online ad market
The U.S. Justice Department has filed a federal lawsuit today against Google for abusing its dominant position in the online advertising market.Sergiu Gatlan (BleepingComputer)