Search
Items tagged with: encryption
No-AI and solid end-to-end encryption is the new tech hype.
If you don't invest heavily in solid end-to-end encryption, privacy-protective and No-AI features, you will be left behind. People might even laugh at you.
Tell everyone.
#NoAI #Encryption #RootForE2EE #Privacy #Tech
1/2 🚨Today, we’re welcoming in Brussels @signalapp's @Mer__edith, @CommissionerHR @dunja_mijatovic & @epfl's @carmelatroncoso among other experts & policymakers to discuss #encryption & privacy.
We're also pleased to have @cdteurope's Iverna McGowan moderate the discussion 🌟 & to hear from Noémie Levain, Legal Expert at @LaQuadrature, Beatriz Ramalho da Silva, Investigative Journalist at @lhreports & Bart Staszewski LGBTI+ activist, founder and chairman of Basta Fundacja 🤩
Standardized, interoperable #encryption is key for a better internet.
Proton and the @ietf OpenPGP Working Group are pleased to announce a crypto refresh of the #OpenPGP standard. Standardization today ensures interoperability tomorrow.
More here ➡️ https://proton.me/blog/openpgp-crypto-refresh.
Modernizing and improving PGP security
Daniel Huigens, the head of Proton’s cryptography team, explains how the latest crypto refresh makes PGP more secure.Daniel Huigens (Proton)
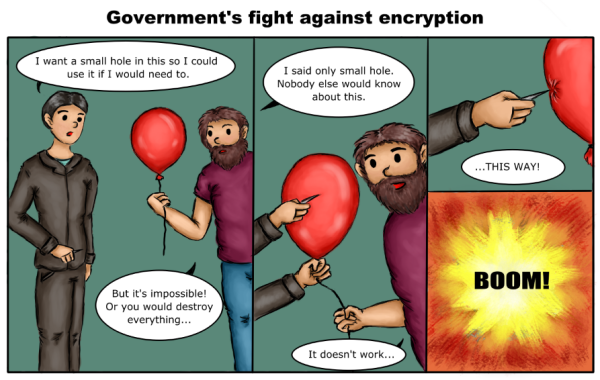
“We should ban doors!” 🚫🚪
Sometimes criminals hide weapons under their clothes.
“We should ban clothes!” 🚫👖
🙃
Do not fall for these misguided arguments.
Most of the time people use end-to-end encrypted apps to talk about the most mundane things.
Sometimes vulnerable people use end-to-end encryption to protect themselves and stay safe.
We should keep and cherish encryption.
We should demand it everywhere.
End-to-end encryption protects our human right to privacy and safety.
We must fight for it! ✊🔒
#RootForE2EE #E2EE #Encryption #Privacy
• any #Fediverse self-hosted instance as easy to set up as a Facebook account
• #Fediverse must easily straddle;
- PRIVATE
consumer individual family safe spaces
#privacy #encryption
– OPENWEB
shared public resource, common carrier status,
actual virtual-public-square not #Elmo absolutist illusion w/corp asses covered by #Section230
• SysAdmin a pain = opportunity
• market for #Privacy enabled
• new Laws needed, incumbents will resist
All this - and more - in the latest episode of the award-winning "Smashing Security" podcast, with me, Carole Theriault, and special guest Mark Stockley.
Thanks to our sponsors @bitwarden, NordLayer, and SecurEnvoy for their support!
https://grahamcluley.com/smashing-security-podcast-308/
#cybersecurity #podcast #ubiquti #databreach #apple #encryption #privacy

Smashing Security podcast #308: Jail after VPN fail, criminal messaging apps, and wolf-crying watches
When Ubiquiti suffered a hack the world assumed it was just a regular security breach, but the truth was much stranger… why are police happy that criminals…Graham Cluley
People have to make a decision. You can only choose one.
Do you want freedom / human autonomy?
Or do you want pretend safety?
Ben Franklin quote:
"Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety."
Thomas Jefferson: "I prefer dangerous freedom over peaceful slavery"
#privacy #humanRights #autonomy #massSurveillance #crypto #e2ee #Signal #encryption quote
https://www.nytimes.com/2022/12/28/opinion/jack-dorseys-twitter-signal-privacy.html
7ha7'5 WHy m4nY Phr33 4ND oP3n 5OURc3 5Of7w4R3 U2e 3NCryP7ION t0 al73r 7ex7 1n70 4 d1ff3r3n7 unr34d4bl3 phoRm@.
Wi7H pHO55 73CHnoLO9Y i H4v3 3ncRYp73D 7HI2 po57 IN 4n 4nci3N7 l337 73CHNo-L4N9U493 (13375p34k) 7O pRO73c7 7h15 M355ag3 PhROM 7ox1c aNd NaZ1 U53R5, ANd 5hOW how N3C3554Ry 7h15 15 1n 7he m0d3rn 3ra.
45 0f n0w, n0 f3d1v3r53 5oF7w4r3 5upPoR72 3ncRyP73d p0575, bu7 I'M 5UR3 IN dU3 7IM3 oUr D34R l34d3R G4GRON 5h4Ll 4N5w3R oUr pr4y3r5!
#FediTips#encryption#leetspeak#Fediverse
https://youtu.be/F3_Y02A53Zc
#matrix #element #decentralization #encryption #webassembly #nodejs #javascript
Matrix Live S07E24 — NodeJS and WASM Bindings for the Rust SDK
Ivan worked on NodeJS and WASM bindings for the rust SDK. What do these words mean? Let's find out! Le menu du jour is in la description ⏬00:00 Hello01:26 Is...YouTube
We all want a secure and trustworthy Internet. In ‘A Digital Dystopia’, @denisersalmeida@twitter.com from @element_hq@twitter.com explains why stopping calls for #encryption backdoors is critical to keeping the world safe online. 🔒
https://www.internetsociety.org/blog/2021/04/a-digital-dystopia-how-calls-for-backdoors-to-encryption-would-ruin-the-internet-for-everyone/
🐦🔗: https://twitter.com/internetsociety/status/1387083635505864707
We're featuring @element_hq@twitter.com as our monthly hot #startup to watch. Meet the founders; learn why.
https://thestack.technology/element-messenger-matrix-protocol-one-to-watch/ #startups #privatemessengers #encryption #opensource #Matrix
🐦🔗: https://twitter.com/StackPublishing/status/1379700799325024257