Search
Items tagged with: cybersecurity
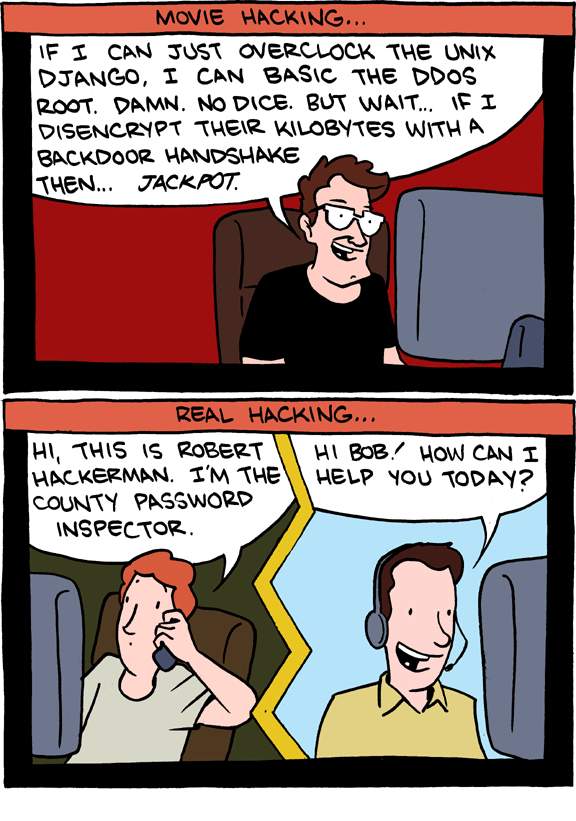
Thinking of this classic* @smbccomics during 'Cybersecurity Awareness Month'
*From 2012 (!?)
Tell you a secret about red team #cybersecurity work:
Almost everyone wants to pretend to be a red teamer; almost nobody has the willingness to put in the real work to become one.
Responsible Red Teaming is @thetaggartinstitute 's most enrolled course by a wide margin.
It is also the least-completed.
The course content is not more technical than any other offensive security course. Indeed, most of it is far less, instead requiring you to think about the human impact of the work. This course discusses how to operate in a safe, appropriate manner. It is not about popping shells.
Once most folks discover this, they bail.
If you want to do offensive security solely because you want to "hack stuff," you're a liability. You must understand your role in hardening defenses and working with defenders to improve operational security.
The job is not a CTF. If you can't hack that, please find another line of work.

The Taggart Institute: Master Your Craft
The Taggart Institute exists to provide low-cost, high-quality technology training to everyone in a welcoming, supportive community.taggartinstitute.org
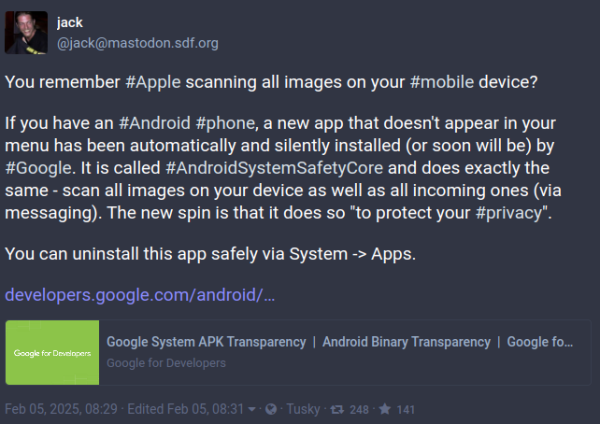
Recent #cybersecurity incident around #CrowdStrike and #Windows #Azure shows the problem around monocultures and control over its one technology.
It is important for Europe to evaluate own dependencies and support administrations, business and citizens alike to run secure IT. For this #softwarefreedom plays an important role.
Turgid members of parliament are excited about their imminent election, but what's that waiting for them in WhatsApp? AI healthcare horrors, and Drew Barrymore.
All this and more in the latest episode of the "Smashing Security" podcast, with me, Carole Theriault, and special guest John Hawes.
Find it in all good podcast apps, or at https://grahamcluley.com/smashing-security-podcast-367/
Thanks to this episode's sponsors - Kolide by 1Password, Kiteworks, and Vanta - for their support!

Smashing Security podcast #367: WhatsApp at Westminster, unhealthy AI, and Drew Barrymore
MPs aren’t just getting excited about an upcoming election, but also the fruity WhatsApp messages they’re receiving, can we trust AI with our health…Graham Cluley
Great news! Amazon has got back to me about the £700 iPhone they failed to deliver (and wouldn't refund or replace) Bad news: what they told me...
Based on this experience, why would anyone buy anything expensive from Amazon ever again? Please share, like and comment if you agree.
Watch my #video.
#amazon #delivery #scam #jeffbezos #cybersecurity
New podcast alert! "Smashing Security" ep 361 is out now, with special guest Paul Ducklin, yours truly, and my erstwhile co-host Carole Theriault.
We discuss how your smartphone may be toast – if you use a hacked wireless charger, we take a closer look at the latest developments in the unfolding LockBit ransomware drama, and Carole dips her toe into online AI romance apps.
https://grahamcluley.com/smashing-security-podcast-361/
#cybersecurity #podcast #malware #ransomware #privacy #romance

Smashing Security podcast #361: Wireless charging woe, AI romance apps, and ransomware revisited
Your smartphone may be toast – if you use a hacked wireless charger, we take a closer look at the latest developments in the unfolding LockBit ransomware drama…Graham Cluley
#cybersecurity zealots often shame humans for writing down their passwords, but as someone who just had to excavate the digital remains of a loved one who died suddenly:
*please* write down your credentials somewhere a trusted human can find them, especially your phone passcode and any primary passwords (like for email accounts, password manager, etc.)
the humans who care about you will need that access for many reasons; a "badass" threat model will only add helplessness to their grief
Oh, go on then...
https://www.smashingsecurity.com/335
#cybersecurity #podcast

335: AI chat wars, and hacker passwords exposed
AI chatbots are under fire in Las Vegas, the secrets of hackers' passwords are put under the microscope, and Graham reveals (possibly) the greatest TV programme of all time.Smashing Security
All this and more is discussed in the latest edition of the "Smashing Security" podcast by cybersecurity veterans Graham Cluley and Carole Theriault.
Warning: This podcast may contain nuts, adult themes, and rude language.
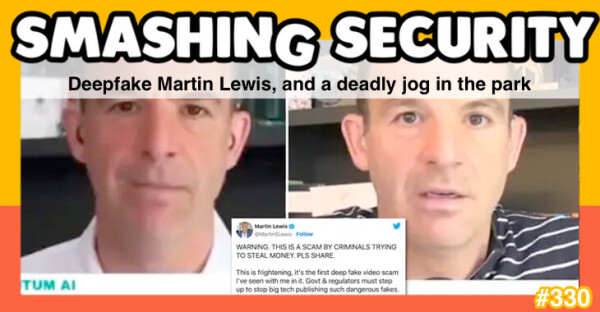
https://grahamcluley.com/smashing-security-podcast-330-deepfake-martin-lewis-and-a-deadly-jog-in-the-park/
#cybersecurity #podcast #deepfake #martinlewis #ukraine #russia
Smashing Security podcast #330: Deepfake Martin Lewis, and a deadly jog in the park
Going for a jog can be bad for your privacy (but even worse for your health), and Britain's consumer finance champion finds his face is being faked.Graham Cluley
It's a brand new "Smashing Security" podcast, with special guest @bittner from The CyberWire!
Find it in all good podcast apps, or at https://www.smashingsecurity.com/326
#cybersecurity #podcast
326: Right Royal security threats and MOVEit mayhem
There are shocking revelations about a US Government data suck-up, historic security breaches at Windsor Castle, and the MOVEit hack causes consternation.Smashing Security

Can you trust ChatGPT’s package recommendations?
ChatGPT can offer coding solutions, but its tendency for hallucination presents attackers with an opportunity. Here's what we learned.Bar Lanyado (Vulcan Cyber)
... what. the. fuck. " https://www.bleepingcomputer.com/news/security/keepass-exploit-helps-retrieve-cleartext-master-password-fix-coming-soon/
#infosec #cybersecurity #passwordmanagers

KeePass exploit helps retrieve cleartext master password, fix coming soon
The popular KeePass password manager is vulnerable to extracting the master password from the application's memory, allowing attackers who compromise a device to retrieve the password even with the database is locked.Bill Toulas (BleepingComputer)
https://crnkovic.dev/testing-converso/
#CyberSecurity #privacy #Signal #WhatsApp

Testing a new encrypted messaging app's extraordinary claims
How I accidentally breached a nonexistent database and found every private key in the Converso app.Crnković (crnkovic.dev)
Smashing Security episode 320: "City Jerks, AI animals, and is the BBC hacking again?"
With @gcluley, Carole Theriault, and special guest @ThomLangford
https://www.smashingsecurity.com/320-city-jerks-ai-animals-and-is-the-bbc-hacking-again/
#cybersecurity #podcast

320: City Jerks, AI animals, and is the BBC hacking again?
Two unsavoury websites suffer from a worrying leak, scientists are going animal crackers over AI, and the BBC is intercepting scammers' live phone calls with victims.Smashing Security
All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by @gcluley and Carole Theriault, joined this week by @varmazis
Find it in all good podcast apps, or at https://www.smashingsecurity.com/319
#cybersecurity #finland #strava #privacy #databreach #mentalhealth #tiktok
319: The CEO who also ran IT, Strava strife, and TikTok tall tales
A boss is bitten in the bottom after being struck by one of the worst crimes in Finnish history, Strava's privacy isn't so private, and a private investigator uncovers some TikTok tall tales.Smashing Security
Find the show in all good podcast apps, or at https://grahamcluley.com/smashing-security-podcast-318/
#cybersecurity #podcast #Tesla #scam #China
Smashing Security podcast #318: Tesla workers spy on drivers, and Operation Fox Hunt scams
Graham wonders what would happen if his bouncing buttocks were captured on camera by a Tesla employee, and we take a look at canny scams connected to China'Graham Cluley
On Firefox, I recommend you to disable the protocoll until we find a solution to either spoof it or break the fingerprinting method. It works even without #javascript.
The whitepaper 👉 https://www.blackhat.com/docs/eu-17/materials/eu-17-Shuster-Passive-Fingerprinting-Of-HTTP2-Clients-wp.pdf
#privacy #fingerprinting #infosec #opsec #cybersecurity #http #http2 #browserleaks
Test yourself at https://browserleaks.com/http2
HTTP/2 Fingerprinting
HTTP/2 Browser Fingerprinting identifies web clients by analyzing specific HTTP/2 attributes, such as SETTINGS frame values, WINDOW_UPDATE frames, stream prioritization, and the pseudo-header fields order.BrowserLeaks
https://grahamcluley.com/smashing-security-podcast-317/
#cybersecurity #juicejacking #ai #chatbot #chatgpt #uber #databreach #podcast
Smashing Security podcast #317: Another Uber SNAFU, an AI chatbot quiz, and is juice-jacking genuine?
Everyone's talking juice-jacking – but has anyone ever been juice-jacked? Uber suffers yet another data breach, but it hasn't been hacked. And Carole hosts the…Graham Cluley
Find "Smashing Security" in your favourite podcast app such as Apple Podcasts or Spotify, or listen at
https://www.smashingsecurity.com/314
#cybersecurity #podcast #tiktok #android #vulnerability #scam
314: Photo cropping bombshell, TikTok debates, and real estate scams
It could be a case of aCropalypse now for Google Pixel users, there's a warning for house buyers, and just why is TikTok being singled out for privacy concerns?All this and much much more is discussed in the latest edition of the "Smashing Security" …Smashing Security
All this and more is discussed in the latest edition of the “Smashing Security” podcast by me and my partner-in-pod Carole Theriault.
Warning: This #cybersecurity #podcast may contain nuts, adult themes, and rude language.
https://grahamcluley.com/smashing-security-podcast-313/
Smashing Security podcast #313: Tesla twins and deepfake dramas
The twisted tale of the two Teslas, and a deepfake sandwich. All this and more is discussed in the latest edition of the "Smashing Security"Graham Cluley
All this and more is discussed in the latest edition of the “Smashing Security” podcast by computer security veterans @gcluley and Carole Theriault.
https://player.captivate.fm/episode/721b532f-a9d8-4b0b-86cb-91f3f5b40e14/
#cybersecurity #podcast #tesla #deepfake

Tesla twins and deepfake dramas
Smashing SecurityThe twisted tale of the two Teslas, and a deepfake sandwich.
All this and more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham...
Not forgetting my co-host through over 300 episodes, Carole Theriault!
Find all their contributions at https://www.smashingsecurity.com, or in your favourite podcast app.
Smashing Security podcast
News and views from the world of cybersecurity, hacking, and internet threats A helpful and hilarious take on the week's tech SNAFUs.Smashing Security
All this - and more - in the latest episode of the award-winning "Smashing Security" podcast, with me, Carole Theriault, and special guest Mark Stockley.
Thanks to our sponsors @bitwarden, NordLayer, and SecurEnvoy for their support!
https://grahamcluley.com/smashing-security-podcast-308/
#cybersecurity #podcast #ubiquti #databreach #apple #encryption #privacy

Smashing Security podcast #308: Jail after VPN fail, criminal messaging apps, and wolf-crying watches
When Ubiquiti suffered a hack the world assumed it was just a regular security breach, but the truth was much stranger… why are police happy that criminals…Graham Cluley
More details:
https://updatedsecurity.com/topic/291-huge-increase-in-malicious-advertising-on-google/?a=1
#infosec #cybersecurity #malware

Huge Increase in Malicious Advertising on Google
It seems like after Microsoft moved to limit Office Macros, there has been a resurgence in other techniques such as malvertising and iso attachments.MalwareTech (UpdatedSecurity)
With special guest @bjmendelson!
https://player.captivate.fm/episode/3db07726-f55a-4742-b2d5-e197ac4cb185/
#cybersecurity #podcast

Norton unlocked, and police leaks
Smashing SecurityCarole's in her sick bed, which leaves Graham in charge of the good ship "Smashing Security" as it navigates the choppy seas of credential stuffing and avoids the swirling waters of apps being...
Read my article on the Tripwire blog:
https://www.tripwire.com/state-of-security/ai-generated-phishing-attacks-are-becoming-more-convincing
#GPT3 #cybersecurity #phishing #businessemailcompromise
AI-generated phishing attacks are becoming more convincing | Tripwire
It's time for you and your colleagues to become more skeptical about what you read. That's a takeaway from a series of experiments undertaken using GPT-3 AI text-generating interfaces to create malicious messages designed to spear-phish, scam, harras…www.tripwire.com
It's not your typical #cybersecurity #podcast.
https://grahamcluley.com/smashing-security-podcast-304/
Smashing Security podcast #304: Oxford’s dating disaster, cheap security robots, and faking a suicide
Someone called OxShagger thinks he has come up with the perfect Valentine’s surprise for Oxford students, but is the way he has gone about “bookworms with…Graham Cluley

Cybersecurity Anti-Predictions for 2023 - Andrew Plato - Medium
Every December, the annual flood of cybersecurity predictions washes across social media. With each passing year these predictions remain wholly predictable. How many times have you heard some…Andrew Plato (Medium)
Interesting read: https://checkmarx.com/blog/starjacking-making-your-new-open-source-package-popular-in-a-snap/
#Python #CyberSecurity #OpenSource

StarJacking - Making Your New Open Source Package Popular in a Snap | Checkmarx.com
Checkmarx supply chain security has recently found a malicious PyPi package with more than 70,000 downloads using a technique we dubbed StarJacking - a way to make an open source package instantly look popular by abusing the lack of validation betwee…Tzachi Zornstein (Checkmarx)
It's the last "Smashing Security" #podcast of the year!
Thanks to special guest @iainthomson for joining us for the fun. 😀
Find it in all good podcast apps, or at
https://grahamcluley.com/smashing-security-podcast-303/
#cybersecurity
Smashing Security podcast #303: Secret Roomba snaps, Christmas cab scams, and the future of AI
Beware your Roomba's roving eye, the Finns warn of AI threats around the corner, and watch out when hailing a cab in Dublin… All this and much more is…Graham Cluley
There's a tool to look at #HackerNews authors and see if their writing is similar to another user (sock puppets anyone?)
This of course leads to larger discussions about #privacy, #cybersecurity, #impersonation, and of course, #shakespeare
https://opensourcesecurity.io/2022/12/04/episode-352-stylometry-removes-anonymity/

Episode 352 – Stylometry removes anonymity
Josh and Kurt talk about a new tool that can do Stylometry analysis of Hacker News authors. The availability of such tools makes anonymity much harder on the Internet, but it’s also not unexp…Open Source Security
We discuss why deleting your Twitter account may be a very bad idea, how the police unravelled the #iSpoof fraud gang, and take a trip into interplanetary file-systems.
Find "Smashing Security" in your favourite podcast app, or listen at https://www.smashingsecurity.com/300
Thanks to everyone who has listened, appeared on the show, or supported us! 🙏
#cybersecurity #twitter #ipfs #phishing #privacy
300: Interplanetary file systems, iSpoof, and don't delete Twitter
Why deleting your Twitter account may be a very bad idea, how the police unravelled the iSpoof fraud gang, and a trip into outer space (or at least interplanetary file systems).Smashing Security
This week #deepfake shenanigans strike users of troubled crypto firm #FTX, the perils of charging your electric vehicle, and is Microsoft’s takeover of Activision good news for video game fanatics.
All this and much much more...
Find @smashingsecurity in your favourite #podcast app or listen to the latest episode at https://www.smashingsecurity.com/299
#cybersecurity #cryptocurrency
299: EV charging risks, FTX, and an ancient apocalypse
Deepfake shenanigans strike users of troubled crypto firm FTX, the perils of charging your electric vehicle, and is Microsoft's takeover of Activision good news for video game fanatics.Smashing Security
Find it in your favourite podcast app, or at https://www.smashingsecurity.com/298
#RIPTwitter #2FA #podcast #cybersecurity #smashingsecurity
298: Housing market scams, Twitter 2FA, and the fesshole
Elon Musk is still causing chaos at Twitter (and it's beginning to impact users), are scammers selling your house without your permission, and Google gets stung with a record-breaking fine.Smashing Security