Search
Items tagged with: Twitter
Moin! In letzter Zeit lese ich immer wieder von #Feditreffen. 🤔Könntest Du Dich grundsätzlich für sowas in #Kiel begeistern? 😃
Wen würde das noch interessieren? Nur mal so als grobe Abfrage, ob das 3, 30 oder 300 Menschen interessiert. 😬
Noch besser würde mir das übrigens in #Eckernförde passen. 😇 Da hatte ich mein erstes und einziges #Twittertreffen mit sehr lieben Menschen! War ein schöner Klönschnackabend. 😊
#Feditreff #Norden #Norddeutschland #SchleswigHolstein #Hamburg #Twitter #fedikiel
Nice. How to leave #X / #Twitter and #Instagram? In the edition of tomorrow‘s newspaper Augsburger Allgemeine offers valuable tips and highlights alternatives in the #Fediverse, such as #Mastodon and #Pixelfed.
A must-read especially for @Gargron from @Mastodon and @dansup from @PixelFed and of course @helpers / @admins
📖 Read more here in german language: https://www.augsburger-allgemeine.de/geld-leben/social-media-alternativen-bluesky-signal-co-neustart-ohne-x-und-meta-104511246
#SocialMedia #Privacy #Alternatives #Mastodon #Pixelfed #Fediverse

Social-Media-Alternativen: Bluesky, Signal & Co: Neustart ohne X und Meta
Sie hadern mit Elon Musks Kurznachrichtendienst X und sind auch nicht mehr glücklich mit all dem, was Mark Zuckerbergs Meta-Konzern anbietet? Kein Problem. Es gibt Alternativen.Von Dirk Averesch, dpa (Augsburger Allgemeine)
Nice. How to leave #X / #Twitter and #Instagram? In the edition of tomorrow‘s newspaper Augsburger Allgemeine offers valuable tips and highlights alternatives in the #Fediverse, such as #Mastodon and #Pixelfed. A must-read especially for @Gargron from @Mastodon and @dansup from @PixelFed and of course @helpers / @admins
📖 Read more here in german language: https://www.augsburger-allgemeine.de/geld-leben/social-media-alternativen-bluesky-signal-co-neustart-ohne-x-und-meta-104511246
#SocialMedia #Privacy #Alternatives #Mastodon #Pixelfed #Fediverse
Social-Media-Alternativen: Bluesky, Signal & Co: Neustart ohne X und Meta
Sie hadern mit Elon Musks Kurznachrichtendienst X und sind auch nicht mehr glücklich mit all dem, was Mark Zuckerbergs Meta-Konzern anbietet? Kein Problem. Es gibt Alternativen.Von Dirk Averesch, dpa (Augsburger Allgemeine)
"Meta and X are going rogue:" European Digital Rights group (EDRi) urges EU to invest in infrastructure "like Mastodon, Peertube and other key pieces of the Fediverse" to secure Europe's independence
https://edri.org/our-work/meta-and-x-are-going-rogue-here-is-what-europe-should-do-now
#news #tech #technology #socialmedia #twitter #fediverse #politics #europe

Meta and X are going rogue. Here is what Europe should do now. - European Digital Rights (EDRi)
To solve the core problem, we have to curb the immense grip Big Tech has on our institutions and invest in independent digital alternatives.European Digital Rights (EDRi)
Research question for those of you who came to the #fediverse after mostly using mainstream #socialMedia like #youtube #instagram #facebook #tiktok #Twitter etc--
what was the final straw that finally got you to make an account here?
Did it take you a while to figure out how the fediverse works, or did you take to it right away?
Do you still use mainstream social media? How often do you post there vs here?
And finally, what is your level of tech expertise? Were/are you already a tech expert (programmer, web developer, "protocol user," whatever you want to call it)?
Anyone used #Friendica? My wife @redbunhead.bsky.social discovered it when I told her about #Pixelfed.
I left #Facebook ~8yr ago & then #twitter for #mastodon. She’s on #FB & #Instagram & is exploring #BlueSky. We both just joined #Substack.
We’re looking for good decentralized social networks that aren’t owned by billionaires. I miss the FB feel sometimes, so any info on Friendica is appreciated.
Wife would also appreciate tips on choosing a Pixelfed server.
Defeating Coordinated Inauthentic Behavior at Scale
Over the weekend, the YouTube channel SmarterEveryDay posted this video (part 1 of a 3-part series) discussing coordinated inauthentic behavior (via crappy content generation) to manipulate YouTube’s…Soatok Dreamseeker (Medium)
Exactly two years ago, we started to post links on #Mastodon via our account @heiseonline 👇
https://mastodon.social/@heiseonline/109314036284496776
It took longer, than I expected, but here we are: it seems like this account now brings continuously more #traffic to heise.de than #X (#Twitter) in its entirety, although it only has ¼ of the follower number (and many of them don't seem to be active anymore).
I'll prepare some graphs after the weekend.
#SocialMedia
#TwitterExodus
#MastodonMigration
#TwitterMigration
#Fediverse
BREAKING!
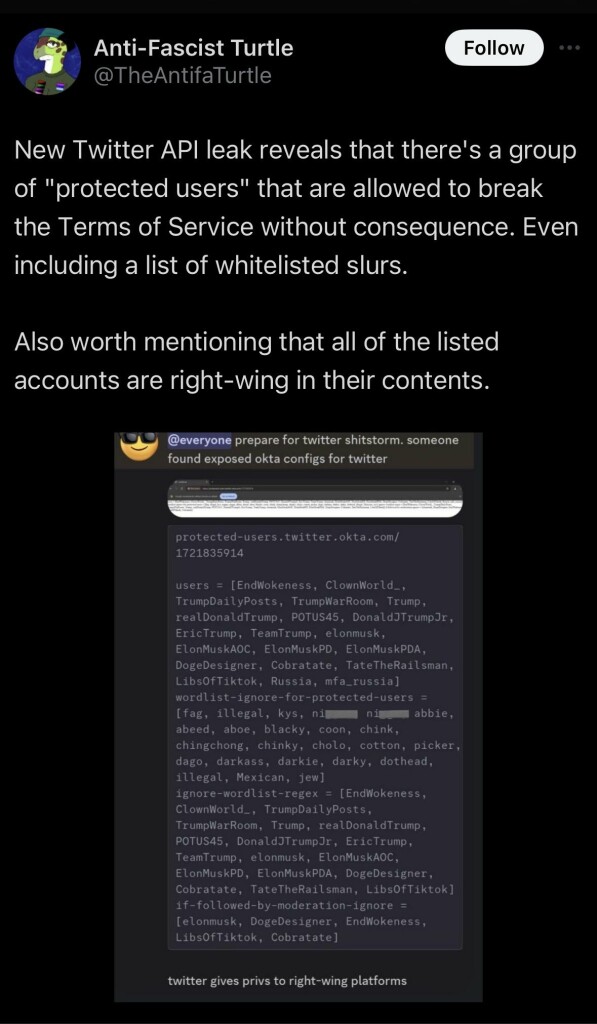
The Antifa Turtle on #Twitter shared a Twitter API okta leak that shows there is a list of "protected accounts", all of them right wing, who are allowed to break #X Terms Of Services without consequence and includes a list of whitelisted slurs they are allowed to use.
The whistle-blowing Twitter account was suspended by mods shortly after.
#elonmusk #freespeech #whistleblower #leak @UnicornRiot @freedomofpress @OffTheHook
On the Twitter blocking follows to Harris2024 account on announcement day:
a. Nadler is right about the asymmetry of every hiccup like this the GOP launches investigation if they don't go along with this.
b. I doubt this was intentional by Musk but definitely a by-product if him cutting staff to the bone so they or the infrastructure couldn't respond to it accordingly.
c. Since Musk didn't step in to fix it immediately like he does whenever a groyper, right wing edgelord, or Nazi shreeks at much smaller issues it is still proof of his desire to have Twitter be explicitly a right wing vomit hose. At the very least Twitter users should create primary accounts on the fediverse (Mastodon, Bluesky, even eek Threads) and at most secondarily post to Twitter.
#ElonMusk #Twitter #Election2024

Nadler urges investigation into X restriction on Kamala Harris account
Rep. Jerrold Nadler urged the House Judiciary Committee to investigate whether Elon Musk’s X prevented users from following a campaign account for Kamala Harris.Kat Tenbarge (NBC News)
A bus crashed into a shop in London. Two people were reportedly hurt, but obviously the incident could have been worse. An X user named Mark Arby took close photos of the crash, and companies then relentlessly kept asking him for permission to use the photos. A lot of other netizens also wanted to make sure if he was ok.
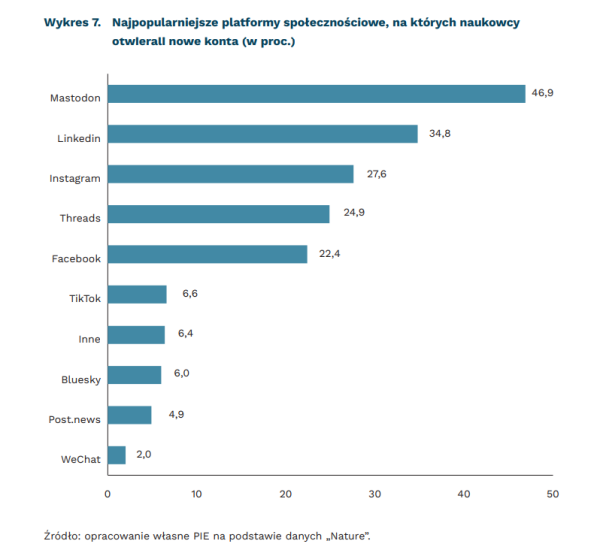
Polski Instytut Ekonomiczny:
📌Naukowcy migrują z X (dawniej Twitter) na inne platformy społecznościowe
➡46,9 proc. nowych kont zostało utworzonych na Mastodonie
➡ 34,8 proc nowych kont utworzono na Linkedin
Blisko połowa ankietowanych osób (47,7 proc.) twierdzi,
że w ostatnich sześciu miesiącach rzadziej korzystało z X, a 6,7 proc. w ogóle przestało
korzystać z platformy
https://pie.net.pl/wp-content/uploads/2023/09/Tygodnik-PIE_36-2023.pdf
Your Twitter/X account is a microphone connected to a mixer controlled by a fascist. You can speak all you want. The fascist controls your volume and can mute you whenever he wants. And you might not even know you’ve been muted because you can still hear yourself in your headphones.
It’s not called resistance when your volume knob is in someone else’s hand.
community feedback, while listening to feedback from former #Twitter users who are rejecting #Mastodon due to the lack of this feature.
Also @alex how hard is functional search to actually integrate? I couldn’t imagine it being that hard, but you’ve done it before, so I’m sure you’d know better than me.
users have been begging for this features for years, and the devs have ignored them consistently. The only reason they are acquiescing now is because former #Twitter users are begging for it. The devs seem to care more about disaffected #Twitter user feedback than the feedback of the very #Mastodon users who have helped build #Mastodon up to what it is today.
Is this type of behavior deserving of thanks?
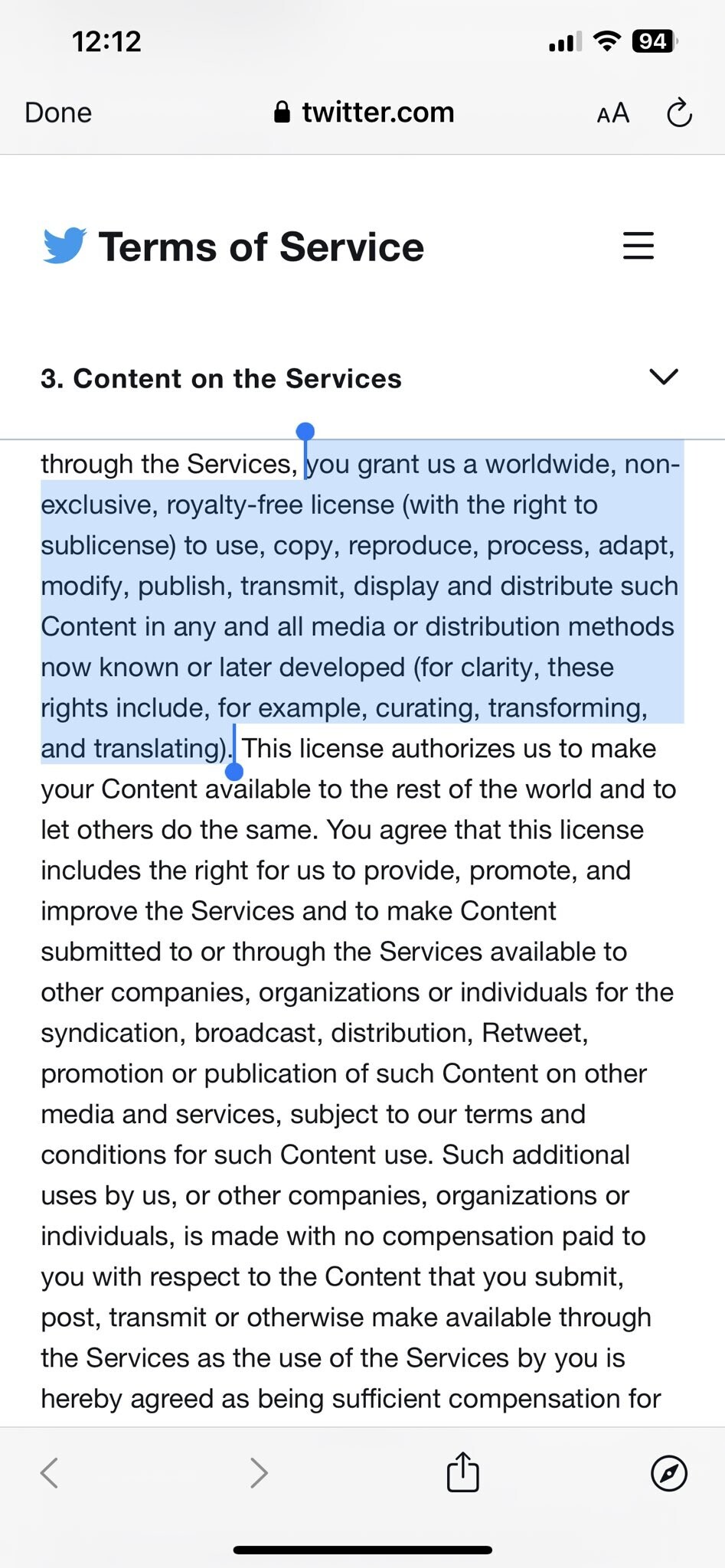
So, Twitter  decided to pull a DeviantArt move and change its Terms Of Services to include anything you post there on their AI dataset, to re-publish your art and benefit from it without your consent or compensation.
decided to pull a DeviantArt move and change its Terms Of Services to include anything you post there on their AI dataset, to re-publish your art and benefit from it without your consent or compensation.
 TIME TO DELETE YOUR ART PORTFOLIO ON TWITTER
TIME TO DELETE YOUR ART PORTFOLIO ON TWITTER 
I will only leave my contact information there, nothing else.
#Twitter #artistsonmastodon #TwitterAlert #AuthorsRights #AI #DeleteTwitter
Musk’s broken promises have yet to reach anything near the volume of lies that Trump told as president. But given his recent track record, it’s well past time for the press to grant him an equal measure of skepticism."
https://www.theverge.com/2023/8/8/23824184/elon-musk-news-coverage-criticism

It’s time to change how we cover Elon Musk
Elon Musk keeps making things up and getting credible headlines out of it. The media needs to be more thoughtful about how they approach the X/Twitter/Tesla/SpaceX CEO.Casey Newton (The Verge)
I'm a full-time indie creator. So I need the platforms to live.

Let's hope mastodon and twitch can cushion the potential fall!
#Kickstarter #Comics #Twitter #Mastodon #IndieComics #Twitch
I noticed that
/circles/none still has some Twitter contacts that I can't remove or delete. I disabled the Twitter connector a long time ago. These contacts are also only visible at /circles/none and there I can't click on "unfollow". Is there any way to remove these contacts? Or can I just do it directly in the database?
"Life is neither static nor unchanging. With no individuality, there can be no change, no adaptation and, in an inherently changing world, any species unable to adapt is also doomed."
Jean M. Auel
No place is perfect, adapt and enjoy with time you will establish your network.
Welcome🫶
#twitter #twitterexodus #fediverse #mastodon #life #newcomer #newhere #welcome
The "left" / "liberal " users of #Twitter will fatten #Mastodon user numbers, whereas the the burning bird on the right might yet rise again like the #Phoenix out of the #Birdsite ashes as #Twitter2.0 (aka #Bluesky.)
Thus it is envisaged by #Elmo and his #PayPal, not-my-friend, @ Jack after #Twitters final demise.
Purefied by fire, only right-wing users and easily gullible #ElmoFanboys will remain on #Bluesky.
https://de.wikipedia.org/wiki/R_%28Programmiersprache%29




 Credit:
Credit:  Credit:
Credit:  (Art by
(Art by  (Art by
(Art by