Search
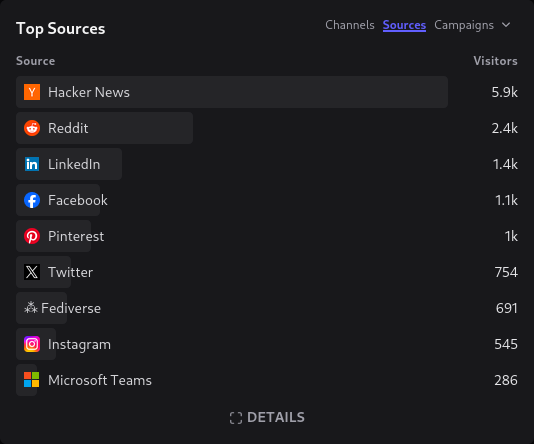
Items tagged with: fediverse
Statt FAQ zu lesen oder sich Videos anzusehen, könnte man einfach ins Gespräch kommen. Daher würde ich gerne wöchentlich einen #FriendicaPlausch abhalten.
Der Termin richtet sich an alle Menschen, die von LinkedIn, Facebook, 𝕏 oder einer anderen unfreien Plattform weg wollen. Die sich für Friendica interessieren, beim Start noch etwas Starthilfe benötigen oder konkrete Fragen zur Anwendung haben.
Der Rahmen:
- Jeden Samstag 14 Uhr
- 45 Minuten Plausch
- Deine Fragen zur Anwendung
- Realisiert über meet.jit.si/FriendicaPlausch
- ohne Cam aber mit Mikrofon
Komm einfach vorbei. Wir lassen uns von den Themen tragen.
#Friendica #Fediverse #DIDit #DUTgemacht #DIDAY
How federated systems dissapear
Long-tail effects mean things become invisible, and it is hard to argue for that which does not seem to exist.
Read more here:
https://test.roelof.info/log/how-federated-systems-dissapear/
Every now and then people break into a fight on here over fediverse vs the Atmosphere (or Bluesky, as its main representative).
I get it. Many of us get frustrated when we see people flocking to a VC-funded fediverse competitor.
But let's focus this energy on making the fediverse a place people want to spend their time in.
Die Penguin Padlock Party ist ein regelmäßig stattfindender Stammtisch jeden dritten Donnerstag im Monat ab 19:00 Uhr auf der c‑base . Sie richtet sich an alle, die sich für freie Software, Datenschutz und digitale Sicherheit interessieren.
Im Mittelpunkt steht die Unterstützung beim Wechsel von Windows auf Linux‑Distributionen – aber die Veranstaltung ist keine reine Linux‑Sprechstunde. Vielmehr bietet sie eine Plattform, um Erfahrungen auszutauschen, voneinander zu lernen und gemeinsam Lösungen zu finden.
Ein wesentlicher Teil der Penguin Padlock Party ist die Cryptoparty‑Komponente: Besucher*innen erfahren, wie sie sich mit geeigneten Tools und Strategien vor digitaler Überwachung schützen können. Dabei werden nicht nur freie und offene Technologien vorgestellt, sondern auch kommerzielle Lösungen, sofern sie zum Schutz der Privatsphäre beitragen.
Die Penguin Padlock Party verbindet technische Hilfe, Wissensaustausch und Bewusstseinsbildung zu Themen wie Datenschutz, Datensicherheit und Datensparsamkeit – in einer offenen und kollegialen Atmosphäre.
Es sind keine Vorkenntnisse notwendig.
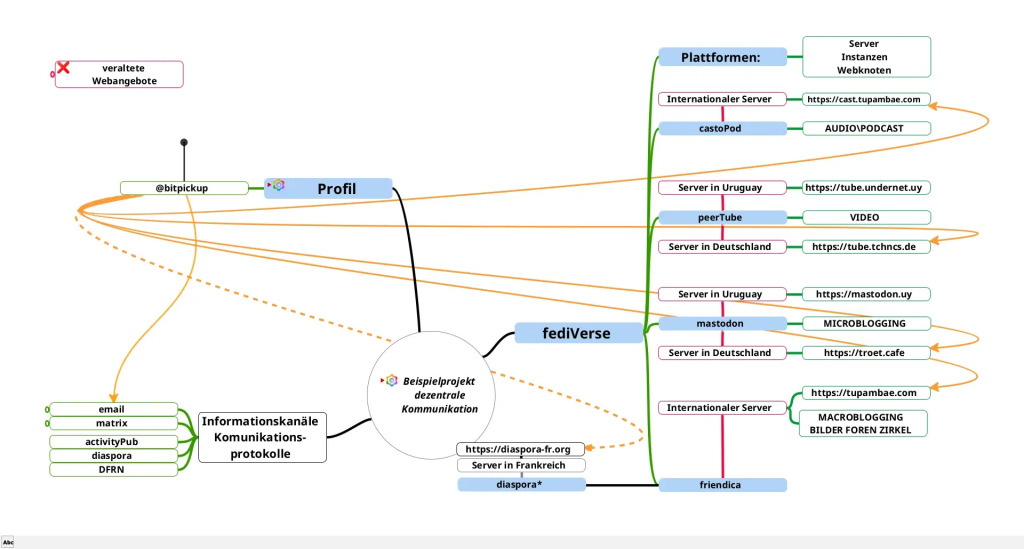
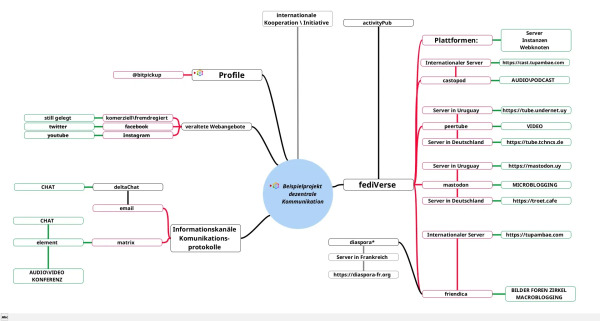
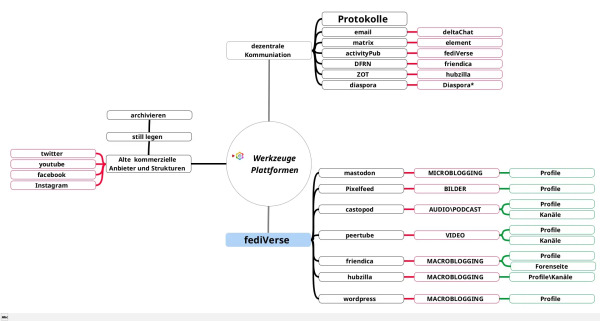
Hey if anyone is interested we setup instances for Mastodon, Pixelfed, Friendica, Peertube, Nextcloud and more, See - https://webape.site/
We do so for a cost so we can afford to also make the many trade-free services and projects we have. See https://tromsite.com/
If you are interested or may want to help, you can also share this. We setup a separate VPS for each instance and provide updates, support, or custom requests as much as we can, for each instance. Plus an email server for each of them.
#fedi #fediverse #mastodon #friendica #nextcloud #foss #opensource #pixelfed #hosting
Und wir schauen zu 😎, echt viele Speaker sind auch auf #Mastodon(#Fediverse).
♲ PSC - 2026-02-15 08:51:16 GMT
🇩🇪 Heute beginnt unser zweiter und letzter Tag der #PSC wieder um 10Uhr.
🎞️Stream: https://youtu.be/YKGb8_RJoU4🎞️Es freut uns euch alle auch heute wieder willkommen zu heißen, egal ob vor Ort auf der #PSC2026 oder im Stream!
Programm des zweiten Tages: events.pirate-secon.net/die-pi…
As the prophecy foretold.
"The site includes stone rings and a possible mastodon carving, possibly dating back 9,000 years when the lakebed was dry."
https://news.artnet.com/art-world/prehistoric-structure-lake-michigan-stonehenge-2432737
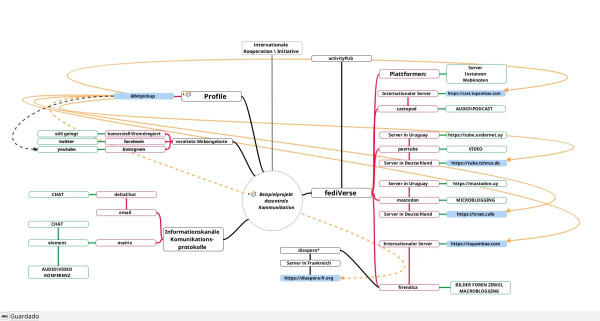
Showing posts across the fediverse by language code
I was investigating the "Channel" feature, and I noticed a channel with the name "Dansk" (Danish). The query is https://friendica.dk/network?channel=language
As far as I can see it gives me a list of posts across the #fediverse with a language specification matching my language settings in my profile. For another one of my accounts (with English specified) the channel is called "English".
Is it possible to create a query/URL (so, not a channel per se) that will give me posts based on a specific language code? So something like
https://friendica.dk/network?language=da (Danish ISO code)
https://friendica.dk/network?language=de (German ISO code)
https://friendica.dk/network?language=en (English ISO code)
Consolidated feeds from specific instances
The Danish part of the #fediverse is characterized by a bunch of small instances - each with a couple of hundred active users on each.
It is possible to set up something in Friendica (maybe a channel?) that gives a consolidated feed of the public posts of some of the Danish instances? The problem I am trying to solve is that we usually promote #fediverse as being able to have a local context, so "if you are interested in music, join Instance A" and "if you like hiking, join Instance B". But these smaller instances tend to drown in the traffic from e.g. mastodon.social, friendi.ca and others.
It would be great if I could set up a feed with "All public posts from these X Danish instances"
Seit vielen Jahren gibt es die ARD/ZDF-Onlinestudie, die nun Medienstudie heißt. Ich habe mir die Studie 2025 mal im Hinblick auf soziale Medien angeschaut mit besonderem Fokus auf das #Fediverse. Erhoben wird dabei allerdings nur der Dienst #Mastodon. Wir schauen uns näher an, wer es wie nutzt!
Ein Thread. 🧵
Kurz noch vorab zur Studie selbst: die Grundgesamtheit ist die deutschsprechende Wohnbevölkerung ab 14 Jahren in Deutschland, Feldzeit war im Frühjahr 2025, n= 2.512, Dual Frame-Stichprobe (d.h. es wurde per Telefon und Online befragt).
#Kommunikationswissenschaft #Science #Medien #SocialMedia #ARD #ZDF #Empirie #Befragung
Gedanken | Basteln an einen neuen Projekt
Ich habe mir in den Kopf gesetzt ein klassisches Forum für SciFi zu machen, so wie es früher einige gab. Gleichzeitig bin ich aber ein absoluter Fan des Fediverse, also musste es etwas sein das beides verbindet. Das Ergebnis bzw. den Ansatz den ich nun verfolge ist ein NodeBB Forum, welches sowohl als klassisches Forum funktioniert und gleichzeitig im Fediverse eingebunden ist. Derzeit findet man es unter scifihub.de aber es ist noch in einen sehr frühen Stadium. Wenn Ihr Ideen dafür habt, oder Lust dabei mitzumachen, meldet Euch gerne bei mir.
#Gedanken #Projekt #SciFi #ScienceFiction #Forum #Fediverse @Science Fiction
Der Fediverse Stammtisch am 2. Februar auf der c-base in Berlin wird leider aufgrund der Witterung, dem BVG Streik und weil einige noch in Brüssel bei der FOSDEM sind
NICHT STATT
Ja, aber die Reichweite?! – Wie wir einst von „Twitter“ ins „Fediverse“ wechselten und es nie bereuten
#Fediverse #Mastodon #Twitter #X #SocialMedia #MicroBlogging #Reichweite #DIDAY #DID #DigitalIndependenceDay #DigitalerUnabhängigkeitstag #DUT
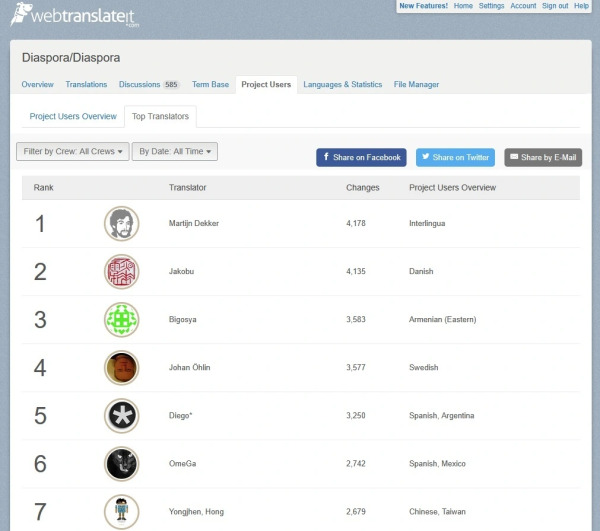
I updated the diaspora* interface translation to my native language: Spanish (Argentina). I'm still in the top 5 on the list of top translators. 😀
Actualicé la traducción de la interfaz de diaspora* a mi idioma nativo, el español de Argentina. Todavía permanezco en el top 5 en la lista de mayores traductores. 😀
#diaspora #pods #dispersion #socialnetwork #social #hello #hola #newhere #freedom #freesoftware #posts #love #mywork #fediverse #podmin #question #publish #home #account #database #network #followme #followyou #users #top #webtranslateit
Software translation and project management · WebTranslateIt
WebTranslateIt is a software localization tool for developers. Includes a project management tool and a translation tool in an easy to use web-based software.webtranslateit.com
Announcement: The 3rd Berlin #Fediverse Day will take place again in Berlin from September 11 to September 13, 2026. 🚀 We are very excited and more information will follow as soon as possible. 👨👨👧👧
- -
Ankündigung, der 3. Berliner Fediverse Day findet vom 11.09.-13.09.2026 wieder in #Berlin statt. 🚀 Wir freuen uns schon sehr und weitere Informationen kommen, asap. 👨👨👧👧
#digitalsovereignty #FOSDEM #FOSDEM2026 #SocialWeb #SocialWebFOSDEM #SocialWebFOSDEM2026
Instance admins: Meta and Twitch have both come out with rules about antisemitism in their latest Terms of Service that are measured but address the concerns of many Jews on the platform.
If I were take those rules and provide you language based on them that would help you implement them on your own sites, would you use it?
FOSDEM 2026 on PeerTube
Content warning: VHSky.cz and MakerTube joined forces to host few FOSDEM rooms on PeerTube as well
Let`s DID it!
Am ersten Sonntag des Monats auf die gute Seite wechseln!
Wir unterstützen dich dabei, deine digitale Autonomie zurückzugewinnen. Gemeinsam und Schritt für Schritt. Ob von X zu Mastodon, von Google Chrome zu Firefox – wir helfen dir beim Wechsel!
Warum nicht einen Email-Dienst mit mehr Privatsphäre probieren? Oder magst du bei einem Kaffee einfach mehr über andere digitale Alternativen erfahren, die unsere Demokratie stärken statt sie zu zerstören? Alternativen, die uns allen eine nachhaltige und selbstbestimmte Teilhabe sichern?
Dann lass uns zusammen loslegen!
Am
Sonntag, 01. Februar 2026
von 12 bis 16 Uhr
freuen wir uns auf dich im
Stadtschloss Moabit
Rostocker Str. 32b, im EG.
Es gibt Tee, Kaffee, Snacks und natürlich Cookies. Lasst uns etwas für unsere digitale Unabhängigkeit tun! Kostenlos, auch ohne Vorkenntnisse. Bring aber gern deine Endgeräte mit.
Der Zugang und der Raum sind barrierefrei.
Eine gemeinsame Aktion von Moabiter Ratschlag e.V. (Stadtschloss Moabit), Digital-Zebra (VÖBB), Topio, dem Hackspace c-base und dem kleindatenverein.
Weitere Informationen: https://di.day
(engl. below)
Als Teil des Digital Independence Day ( https://di.day ) zeigen wir euch das Fediverse.
Einlass: 15 Uhr
Beginn: 16 Uhr
Wir zeigen euch, was es es für alternative Social Media Plattformen im Fediverse gibt
Wir geben euch eine kurze allgemeine Einführung ins Fediverse und zeigen euch Mastodon, Pixelfed, Peertube, Gancio, Loops und andere...
Es werden Leute der folgenden Punk/Hardcore/DIY Fediverse Instanzen vor Ort sein:
Außerdem zeigen wir euch noch https://punkstodon.de und https://punktube.net sowie den Fedi Punk Guide
Mehr infos bekommt ihr hier: https://punx.social/fedi-workshop.html
Bitte verbreitet dieses Event auf Facebook und Instagram, falls ihr dort noch seid!
---------------
As part of Digital Independence Day (https://di.day), we're showing you the Fediverse.
Doors: 3pm
Start: 4pm
We'll show you what alternative social media platforms are available in the Fediverse.
We'll give you a brief general introduction to the Fediverse and show you Mastodon, Pixelfed, Peertube, Gancio, Loops and others...
People from the following punk/hardcore/DIY Fediverse instances will be there:
We will also show you https://punkstodon.de, https://punktube.net and the Fedi Punk Guide
More information at https://punx.social/fedi-workshop.html
Please publish this event on Facebook and Instagram, if you are still there!
Thx to @The_Counterforce for publishing this picture under creative commons
Friendica 2026.01 released !
Just noticed the new friendica version has been released 😀. See https://github.com/friendica/friendica/releases/tag/2026.01
For u3a.social I'll be doing an upgrade on a test instance as soon as I can and then plan for the live upgrade (I'll also want to switch to native rather than docker database).
The nice thing about test upgrades is you get to test your backups !
@U3ACommunities Computing #friendica @Friendica Support #fediverse
Release Friendica 2026.01 released · friendica/friendica
We are very happy to announce the availability of the new stable release of Friendica “Blutwurz" 2026.01. In addition to several improvements and new features, this release contains fixes for secur...GitHub
Are there any "case studies" of whole communities moving to the fediverse, similar to the Forkiverse?
I'm thinking about writing a version of my article https://stefanbohacek.com/blog/fediverse-an-overview-for-government-agencies/ and aim it at community organizers.
Fediverse: An overview for government agencies
Fediverse as a tool for government.Stefan Bohacek (stefanbohacek.com)
On February 3rd (very soon!) I am hosting another [BERLIN FEDERATED NETWORK EXPLORATION CIRCLE] at @offline. It's a chance to meet and talk with people who are interested in the #fediverse & networking & exploration & circ---you get the idea.
We have the pleasure of having @hongminhee who will give a presentation about @fedify "an opinionated #ActivityPub framework for TypeScript that handles the protocol plumbing"
It is an open free event and everyone is welcome!
Das außergewöhnliche am #fediVerse ist @Cheatha, das es die Kapazität besitzt dir ein ums andere mal die Mind weg zu blowen.
Irgendwie kombiniert es semingless dezentral, verknüpft Blickwinkel mit Winkelblicken. Es erschafft am laufenden Band Ansichten die indirekt fast schon zwangsläufige Kreativität erzeugen.
Und damit nicht genug!
In Wirklichkeit ist es noch viel schlimmer.
Die Diversität seiner international verzweigten #häckerSzene mit ihrem anarchistischen Charme produzieret einfach immer wieder neue Gedanken welche deine Lebenszeit in faszinierenden creative outbursts verschwenden.
🤷
CC:
@Claus von Wagner
(sry volks, #altTexte werden Nachgereicht)
SFSCON25 - Tobias Diekershoff - Fediverse: Beyond text in the stream
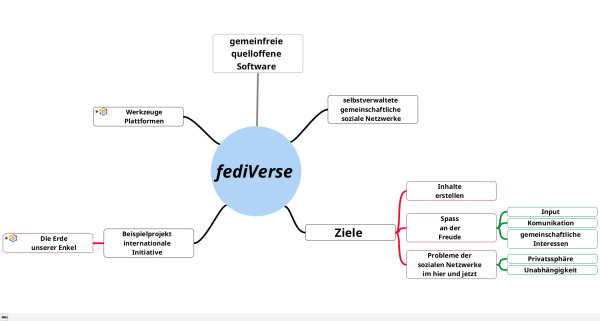
The Fediverse is a large, decentralised social network that continues to grow. Since its beginnings in 2008, text-based platforms such as StatusNet, Friendica and Mastodon have dominated. In this session, we’re going to take a look at what’s out there in the network that’s beyond just text. Starting with well-known video and image-sharing services such as Peertube and Pixelfed, we will explore other projects and the opportunities they offer creative podcasters, streamers and 3d artists.
If you are not familiar with the Fediverse, please watch my presentation from last year, “about:Fediverse“, which will introduce you to this social network alternative.
CLT25: Fediverse: Abseits von Text im Stream
Das Fediverse ist groß und wächst stetig weiter. Seit seinen Anfängen 2008 dominieren textbasierte Plattformen wie StatusNet, Friendica oder heutzutage Mastodon. In diesem Vortrag wollen wir einmal schauen, was es abseits des Formates „Text“ so im Fediverse gibt und wie Kulturschaffende diese Kanäle nutzen können.
Licensed to the public under http://creativecommons.org/licenses/by/4.0
The original video can be viewed here: https://media.ccc.de/v/clt25-238-fediverse-abseits-von-text-im-stream
Fediverse: Abseits von Text im Stream
Das Fediverse ist groß und wächst stetig weiter. Seit seinen Anfängen 2008 dominieren textbasierte Plattformen wie StatusNet, Friendica o...media.ccc.de
Heute war ja der erste #diday und Teil der Idee ist es ja Leute ins #Fediverse zu bekommen. Wir wissen alle, dass das Fediverse groß, unübersichtlich und einschüchternd seit kann.
Eine hervorragende Reihe von Veranstaltungen auf denen man mal "dumme Fragen" stellen kann (keine Bange, die gibt es nicht) firmieren under dem Hashtag #FediTreff - gibt es über ganz Deutschland und die Welt verteilt. Dezentrale Stammtische um über das Fediverse zu schnacken.
Morgen ist es in #Berlin wieder so weit. Da treffen wir uns jeden 1. Montag im Monat auf der @c-base e.V. ab 19 Uhr. Kommt gerne vorbei wenn ihr #NeuHier seit oder jemanden kennt der noch Fragen zum Fediverse klären will, bevor der DiDay im Social Media Bereich angegangen wird.
Here's your chance to see the fediverse platform Bonfire in action (without having to install it or create an account)
Our favorite fedi live streamer, @ozoned is going to be streaming an install and walk through soon (Jan 2 at 8 AM CST).
Add it to your calendars and #JoinIn
https://freestreamers.btfree.org/event/bonfire-install-and-config-livestream
Import Facebook content (pictures) into friendica
!Friendica Support I suggested today on Facebook that people should start using friendica (or, any #fediverse service) instead of Facebook. I was immediately asked:
"What do I do with the 17 years of pictures I have on Facebook?"
I tried to find an answer - hoping that there would be a way similar to the Instagram import feature of pixelfed, but I could not find one.
Is there a way to get all of your content from Facebook imported into friendica? Or do you know of a #fediverse service similar to friendica that has this feature?
Hey #39C3!
Tomorrow, Day 3, 14:00, I will spontaneously be hosting a session in the @cbase Fediverse Assembly on “Lessons from a Public University: Bringing Institutions into the Fediverse” and sharing my experiences from the step-by-step approach at the University of Innsbruck, where we have a Mastodon Instance on our servers, SSO-connected, based on a general strategic approach towards open plattforms.
Happy to see a lot of Fediverse fighters!
https://events.ccc.de/congress/2025/hub/de/event/detail/lessons-from-a-public-university-bringing-institut
![[39c3] Lessons from a Public University: Bringing Institutions into the Fediverse](https://fika.grin.hu/photo/preview/600/554430)
[39c3] Lessons from a Public University: Bringing Institutions into the Fediverse
Was passiert, wenn eine öffentliche Universität beschließt, das Fediverse als Teil eines ganzheitlichen strategischen Ansatzes für die Wissenschaftskommunikation zu nutzen? Ich werde ehrliche Erkenntnisse aus unserer Arbeit an der Universität Inns...39c3