Search
Items tagged with: crypto
The #network from forgotten times when #crypto meant #privacy, not #corruption:
Connect to your friends with #Hyphanet to have a safe haven to coordinate when bad comes to worse.
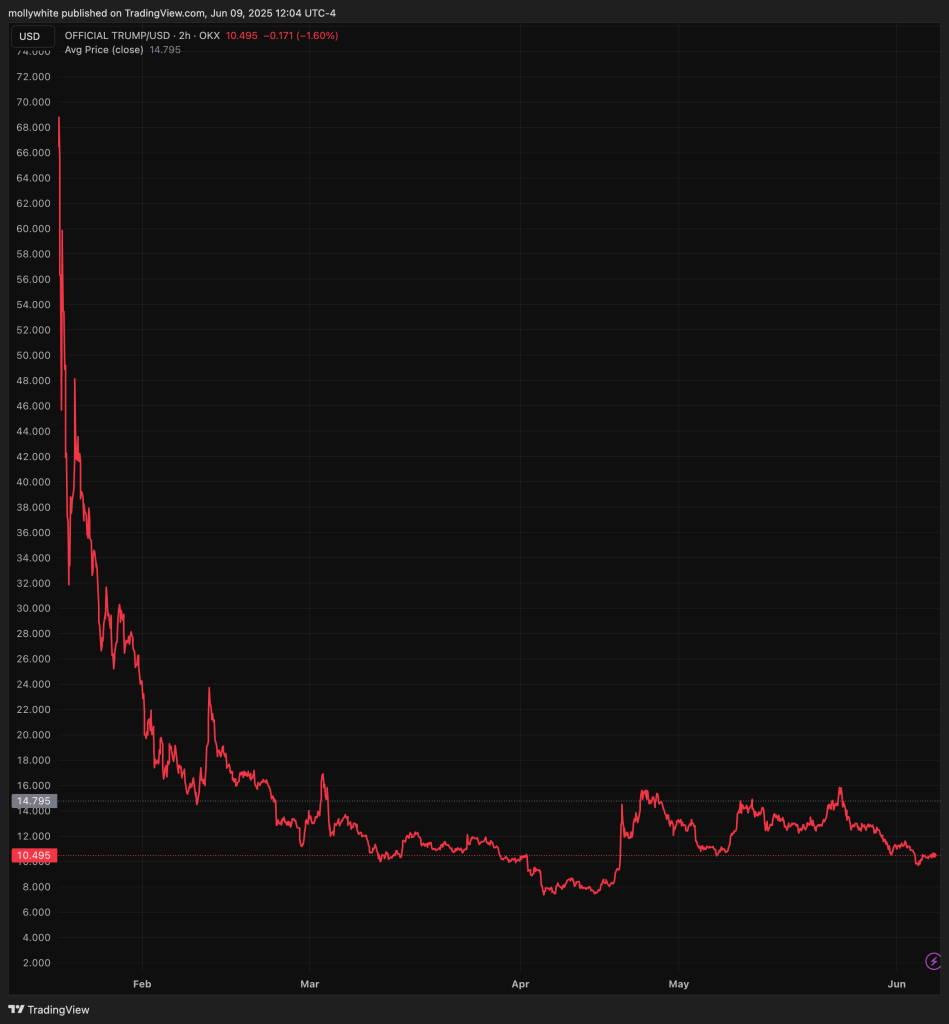
The crypto industry isn’t dead yet. In fact, it’s one of the biggest funders in this US election cycle.
On #TechWontSaveUs, I spoke to @molly0xfff to discuss what crypto boosters want from their nearly $200 million in campaign spending.
Listen to the full episode: https://techwontsave.us/episode/235_crypto_is_spending_millions_to_sway_the_us_election_w_molly_white
#tech #crypto #politics #bitcoin
Crypto Is Spending Millions to Sway the US Election w/ Molly White - Tech Won’t Save Us
A left-wing podcast for better technology and a better world.Tech Won't Save Us
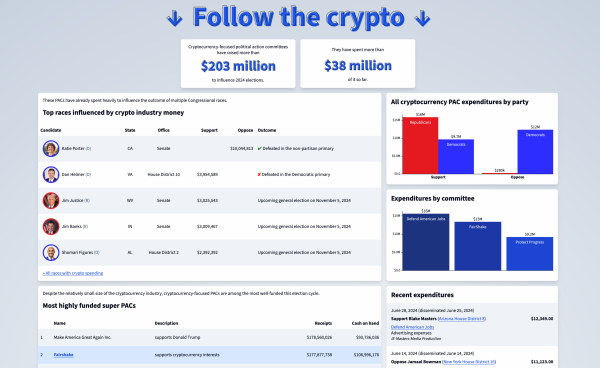
It’s finally time to release my newest project: https://www.followthecrypto.org/
This website provides a real-time lens into the cryptocurrency industry’s efforts to influence 2024 elections in the United States.
#crypto #cryptocurrency #elections #USpol #lobbying
Follow the Crypto
Follow the cryptocurrency industry’s influence on 2024 elections in the United States.Follow the Crypto
#crypto #donation #anonymity #LifeSupport #donationsneeded #MutualAid
I am still waiting for my application for caretaker's social support accepted. I take full-time care of my wife (wheelchair, cerebral palsy) and I hope that - after several appeals and re-appeals (due to unfriendly legislation and even less friendly praxis) - I will get it approved. ETA: 3-6 months.
Meanwhile, I have no income, cannot even work (for money) remotely, as the authorities routinely use odd jobs as an argument (you can work, you do not need social support) to reject such applications.
So, I kindly ask you to support me with some crypto, so I can survive until - hopefully - happy ending.
Here is the regular link to AnonPay service. And here is the Onion link as well.
Bumps, boosts and shares will be appreciated.
When you are a #Linux user and interested in #crypto
https://flathub.org/apps/com.github.miguelmota.Cointop
My reply?
“Thanks but no thanks.”
Why?
Because I don’t need to see the app. I know the people behind it and what they stand for. The app can only ever be a manifestation of (or an initial misdirection from) that.
Expecting the wolf that took a bite out of you last time to this time act in your interests is how you end up as its dinner.
#BlueSky #JackDorsey #billionaires #SiliconValley #decentralisation #lipService #crypto #bullshit
People have to make a decision. You can only choose one.
Do you want freedom / human autonomy?
Or do you want pretend safety?
Ben Franklin quote:
"Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety."
Thomas Jefferson: "I prefer dangerous freedom over peaceful slavery"
#privacy #humanRights #autonomy #massSurveillance #crypto #e2ee #Signal #encryption quote
https://www.nytimes.com/2022/12/28/opinion/jack-dorseys-twitter-signal-privacy.html