Search
Items tagged with: infosec
On Firefox, I recommend you to disable the protocoll until we find a solution to either spoof it or break the fingerprinting method. It works even without #javascript.
The whitepaper 👉 https://www.blackhat.com/docs/eu-17/materials/eu-17-Shuster-Passive-Fingerprinting-Of-HTTP2-Clients-wp.pdf
#privacy #fingerprinting #infosec #opsec #cybersecurity #http #http2 #browserleaks
Test yourself at https://browserleaks.com/http2
HTTP/2 Fingerprinting
HTTP/2 Browser Fingerprinting identifies web clients by analyzing specific HTTP/2 attributes, such as SETTINGS frame values, WINDOW_UPDATE frames, stream prioritization, and the pseudo-header fields order.BrowserLeaks
Update: we seem to be unblocked. Thank you all!
—
Last night, the website of Reykjavík #Hackerspace, Hakkavélin, got flagged by Google's "Safe Browsing" as "deceptive":
https://mstdn.social/@rysiek/110166076666804008
The site is now unblocked. 🎉
But our #Yunohost login page is still blocked:
https://bob.hakkavelin.is/yunohost/sso/ 🤦♀️
We would really appreciate help with reporting this also as incorrect. You can do this here, and it takes less than a minute:
https://safebrowsing.google.com/safebrowsing/report_error/?tpl=mozilla&url=https%3A%2F%2Fbob.hakkavelin.is%2Fyunohost%2Fsso%2F
https://www.pcmag.com/news/openai-confirms-leak-of-chatgpt-conversation-histories
Can you guess who or what does Sam Altman from #OpenAI blame for it?
"A bug in an open source library."
Yup. #FLOSS is great for #OpenAI as a way to build on somebody else's code, and as a way to train their models on somebody else's code. But as soon as shit hits the fan, it *will* get thrown under the bus.
Wanna *bet* it's not an #AGPL library? SV hypercapitalists keep away from those!
#FOSS #InfoSec

OpenAI Confirms Leak of ChatGPT Conversation Histories
OpenAI CEO Sam Altman blames the exposure on 'a bug in an open source library.' A patch has been released, but the chat history sidebar remains inaccessible.Michael Kan (PCMag)
More details:
https://updatedsecurity.com/topic/291-huge-increase-in-malicious-advertising-on-google/?a=1
#infosec #cybersecurity #malware

Huge Increase in Malicious Advertising on Google
It seems like after Microsoft moved to limit Office Macros, there has been a resurgence in other techniques such as malvertising and iso attachments.MalwareTech (UpdatedSecurity)
Journalists, refugees, people at-risk and from marginalized groups, and we all, really, need to *know* that tech people supporting them cannot be legally forced to disclose the (often very personal or sensitive) data they gain access to while providing tech support.
Data that is shared with them in confidence, and which is often necessary to render tech help at all.
#InfoSec #Legal
#OpenSource #passwordManager #LastPass
cc @keepassxc
I think those people have not been at this long.
All companies eventually get hacked. All companies eventually will be breached, and it's not if; it's when.
And if you are a company storing millions of passwords, you better believe you are being attacked constantly.
Given that world, I want a company that:
- is transparent and lets their users know immediately when something is up and gives as many details as they can.
- can actually detect incidents and has a solid process to follow in dealing with them and communicating about them
It merely means they either a) can't detect incidents or b) are hiding them from you
If you are using a password manager that is silent about breaches, near misses, incidents, etc., That should be cause for concern.
Why can't we have nice things?
Microsoft. Microsoft is why we can't have nice things.

Pridefall Discord Attack 2022 | How To Recover From Scams?
Pridefall Discord Attack is a cyber-attack event that takes place on all social media platforms to harass and target the LGBTQ+ community. Read along with this page and you will learn detailed information about the Pridefall Discord Attack 2022.Shivangi Gupta (Pathofex)
https://web.archive.org/web/20180429220059if_/https://twitter.com/tmobileat/status/982187919061303296
#InfoSec #TMobile
T-Mobile Austria on Twitter
“@Korni22 @c_pellegrino @PWTooStrong @Telekom_hilft @Korni22 What if this doesn't happen because our security is amazingly good? ^Käthe”Twitter
https://www.digitalrights.ie/facebook/
#privacy #security #infosec
https://scotthelme.co.uk/introducing-another-free-ca-as-an-alternative-to-lets-encrypt/
It's always good to have alternatives around. ZeroSSL appears to be a European company that now provides free TLS certificates using the ACME protocol.
#TLS #SSL #CA #infosec #letsencrypt
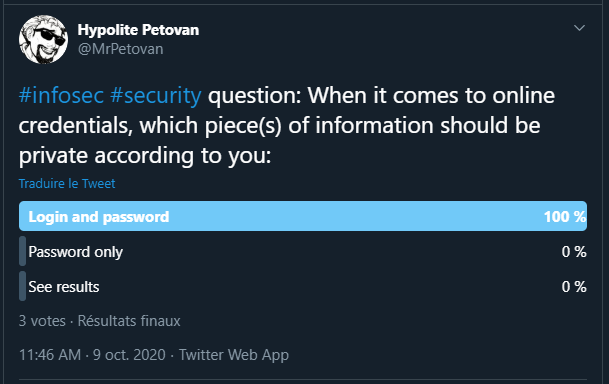
On the privacy of online login forms inputs
I'm surprised but not shocked by this result. It seems to me that many people are confused about why online login forms have two fields but only one of them hides the input.
On one hand, if all the credentials are meant to be private, why not add a third or a fourth input field with more private stuff? This would be more secure, right? On the other hand, if someone is using a weak password, what is the likelihood their login is easily guessable as well?
I personally believe online login forms have two fields for two different kind of data: an identifier that shouldn't be considered private, because the password/phrase field is already there for that specific purpose. As a result, I fully support letting users fill the login field with as many different identifiers they can have, including email addresses and public usernames, because it is massively more convenient without compromising on security since there is a password.