Search
Items tagged with: abuseReporting
Earlier this year, I detailed a simple technique for deanonymizing scam sites on CloudFlare, by getting the back-end webserver to email you and reveal the server’s IP address (so you can forward your complaints to their ISP).
In a similar vein, I’d like to explain a simple technique for increasing the likelihood that your abuse reports on social media websites like Twitter get taken seriously.
Don’t Use the Easy Button
Every tweet (except your own) has a Report Tweet link attached to it. The user interface is different on web and mobile, but most people know how to find it.
The problem with this “easy button” is twofold:
- It’s low-effort and high-bandwidth, so a lot of people use it and therefore the signal-to-noise ratio isn’t very high.
- The “report tweet” workflow lets you select from one of a few narrowly defined categories of abuse without giving you any space to explain why it’s abusive.
For example: A lot of anti-furry hate is a dogwhistle for ableist or queerphobic rhetoric. Without knowing that context, how do you expect the folks handling abuse reports for social media companies to make the correct choice?
Instead, File an Abuse Report
This is actually a separate thing, and the link to the harassment report form is here. (This is one of many forms you can file with Twitter’s support team.)
Not only do you get to click the radio buttons that the Quick and Easy path allows, you also get to fill in a description of the problem.
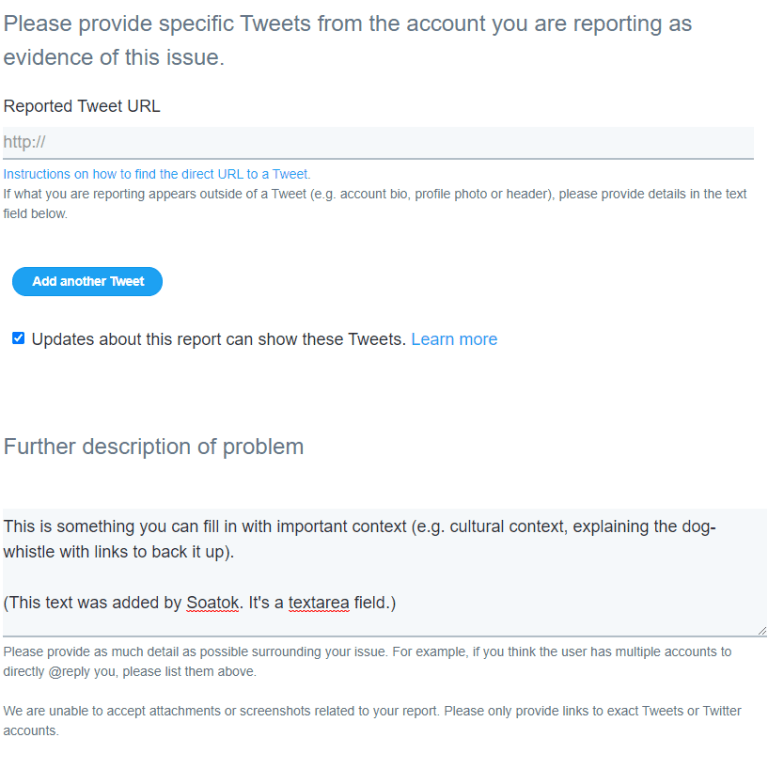
The difference here isn’t theoretical; a concise explanation of the problem is the difference between your report being ignored and this:
https://twitter.com/SoatokDhole/status/1319983706858246146
If you have any friends that are frequent targets of social media harassment, and their reports aren’t taken seriously, share this article with them.

(That being said, I’m really sorry this is even necessary.)
What About Automation?
One motivation to still use the “easy button” when reporting abuse is if you’re hoping to trigger some automated mechanism (i.e. “If 3 different accounts report this as abuse, suspend their account until someone can investigate”).
In that case, press that easy button to your heart’s content.
https://twitter.com/packonines/status/1068746663764860929
https://soatok.blog/2020/11/12/deplatforming-hate-and-harassment/
#abuseReporting #cyberbullying #harassment #hateSpeech #onlineAbuse #SocialMedia #Twitter
Update (2021-01-09): There’s a newer blog post that covers different CloudFlare deanonymization techniques (with a real world case study).Furry Twitter is currently abuzz about a new site selling knock-off fursuits and illegally using photos from the owners of the actual fursuits without permission.
Understandably, the photographers and fursuiters whose work was ripped off by this website are upset and would like to exercise their legal recourse (i.e. DMCA takedown emails) of the scam site, but there’s a wrinkle:
Their contact info isn’t in DNS and their website is hosted behind CloudFlare.
CloudFlare.
Private DNS registration.
You might think this is a show-stopper, but I’m going to show you how to get their server’s real IP address in one easy step.
Ordering the Server’s IP Address by Mail
Most knock-off site operators will choose open source eCommerce platforms like Magento, WooCommerce, and OpenCart, which usually have a mechanism for customers to register for an account and login.Usually this mechanism sends you an email when you authenticate.
(If it doesn’t, logout and use the “reset password” feature, which will almost certainly send you an email.)
Once you have an email from the scam site, you’re going to need to view the email headers.
With Gmail, can click the three dots on the right of an email then click “Show original”.
Account registration email.
Full email headers after clicking “Show original”.
And there you have it. The IP address of the server behind CloudFlare delivered piping hot to your inbox in 30 minutes or less, or your money back.
That’s a fairer deal than any of these knock-off fursuit sites will give you.
Black magic and piss-poor opsec.
What Can We Do With The Server IP?
You can identify who hosts their website. (In this case, it’s a company called Net Minders.)With this knowledge in mind, you can send an email to their web hosting provider, citing the Digital Millennium Copyright Act.
One or two emails might get ignored, but discarding hundreds of distinct complaint emails from different people is bad for business. This (along with similar abuse complaints to the domain registrar, which isn’t obscured by DNS Privacy) should be enough to shut down these illicit websites.
The more you know!
Epilogue
https://twitter.com/Mochiroo/status/1259289385876373504The technique is simple, effective, and portable. Use it whenever someone tries to prop up another website to peddle knock-off goods and tries to hide behind CloudFlare.
https://soatok.blog/2020/05/09/how-to-de-anonymize-scam-knock-off-sites-hiding-behind-cloudflare/
#cloudflare #deanonymize #DNS #fursuitScamSites #informationSecurity #OnlinePrivacy #opsec