Search
Items tagged with: http
Ok - I've been told that HTTP 418 belongs in the 400 block because it's the same as requesting a non-existent file. This argument claims that 418 is the same as 404.
I tend to think of 418 as being more analogous to 501. You cannot put coffee in a teapot, which is a statement about the teapot.
On Firefox, I recommend you to disable the protocoll until we find a solution to either spoof it or break the fingerprinting method. It works even without #javascript.
The whitepaper 👉 https://www.blackhat.com/docs/eu-17/materials/eu-17-Shuster-Passive-Fingerprinting-Of-HTTP2-Clients-wp.pdf
#privacy #fingerprinting #infosec #opsec #cybersecurity #http #http2 #browserleaks
Test yourself at https://browserleaks.com/http2
HTTP/2 Fingerprinting
HTTP/2 Browser Fingerprinting identifies web clients by analyzing specific HTTP/2 attributes, such as SETTINGS frame values, WINDOW_UPDATE frames, stream prioritization, and the pseudo-header fields order.BrowserLeaks
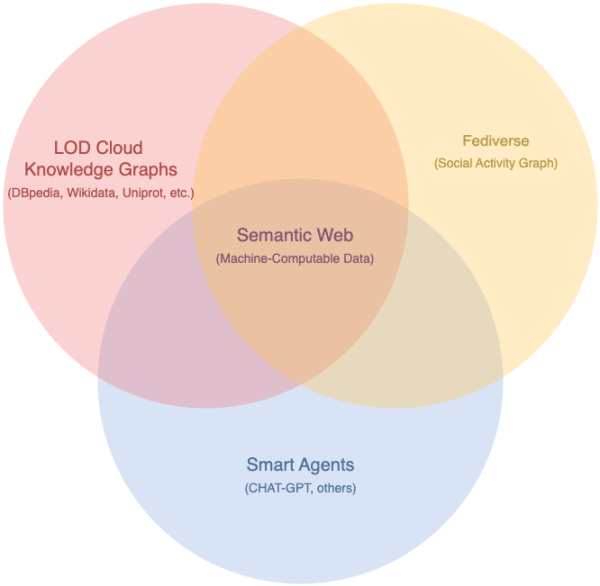
A hashtag is the fundamental unit of Web Magic, once understood. Basically, name things using hyperlinks (ideally, #HTTP variety) and connectivity magic happens, at Web-scale.
The #Fediverse itself is the latest demonstration of said magic, courtesy of #ActivityStreams 😀
#Web30 #SocialMedia #LinkedData #SemanticWeb