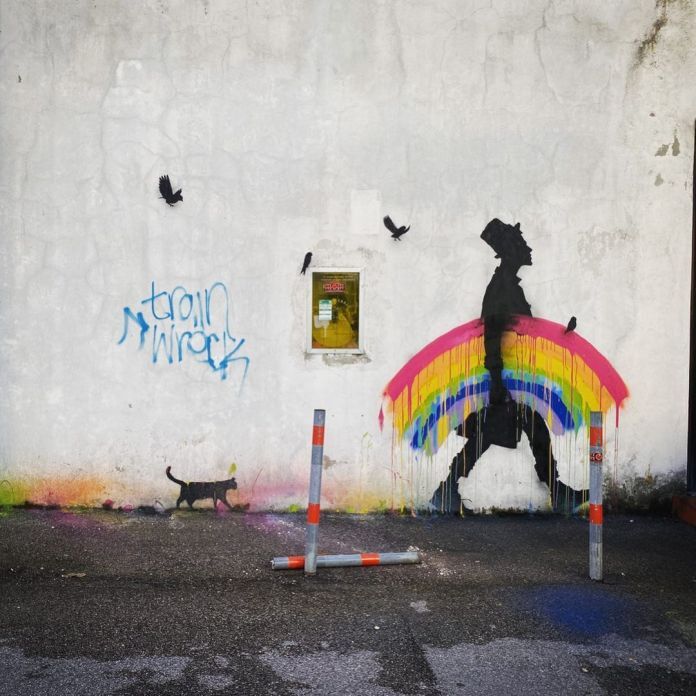Search
Items tagged with: rainbow
Rainbow Carrier – By Kenny Random
By Kenny Random in Padova, Italy.
Follow Kenny Random: Instagram // Facebook // Random Gallery
More by Kenny Random on Street Art Utopia
Rainbow Staircase by Maratto in Arzachena, Sardinia, Italy

By Manuel Maratto in Arzachena, Sardinia, Italy.


Comments:
https://twitter.com/StreetArtUtopia/status/1541452566269132801
Login • Instagram
Welcome back to Instagram. Sign in to check out what your friends, family & interests have been capturing & sharing around the world.www.instagram.com